President Donald Trump has promised to implement “extreme vetting” of immigrants and foreign travelers, asserting that widespread vetting failures had allowed many terrorists to enter the United States. This policy analysis provides the first estimate of the number of terrorism vetting failures, both before and after the vetting enhancements implemented in response to the September 11, 2001, attacks. Vetting failures are rare and have become much rarer since 9/11.
A terrorism vetting failure occurs when a foreigner is granted entry to the United States who had terrorist associations or sympathies and who later committed a terrorism offense including support for terrorist groups abroad. This analysis defines vetting failure broadly to include individuals who had privately held extremist views before entry. Moreover, unless evidence exists to the contrary, it assumes that anyone who entered the United States legally either as an adult or older teenager, and who was charged with a terrorism offense within adecade of entry, entered as a result of a vetting failure, even without any evidence that he or she was radicalized prior to entry.
By this definition, only 13 people — 2 percent of the 531 individuals convicted of terrorism offenses or killed while committing an offense since 9/11 — entered due to a vetting failure in the post‑9/11 security system. There were 52 vetting failures in the 15 years leading up to 9/11, four times as many as in the 15 years since the attacks. From 2002 to 2016, the vetting system failed and permitted the entry of 1 radicalized terrorist for every 29 million visa or status approvals. This rate was 84 percent lower than during the 15-year period leading up to the 9/11 attacks. Only 1 of the 13 post‑9/11 vetting failures resulted in a deadly attack in the United States. Thus, the rate for deadly terrorists was 1 for every 379 million visa or status approvals from 2002 through 2016.
During this same period, the chance of an American being killed in an attack committed by a terrorist who entered as a result of a vetting failure was 1 in 328 million per year. The risk from vetting failures was 99.5 percent lower during this period than during the 15-year period from 1987 to 2001. The evidence indicates that the U.S. vetting system is already “extreme” enough to handle the challenge of foreign terrorist infiltration.
Introduction
Soon after assuming office, President Donald Trump signed an executive order that temporarily suspended all refugee admissions as well as immigration and travel of nationals of several Middle Eastern and North African countries. This order, and its two successors, claimed to institute the ban to "ensure that adequate standards are established to prevent infiltration by foreign terrorists."1 Yet it provided no evidence that the previous standards were inadequate.
Since the September 11, 2001 terrorist attacks, the federal government has poured substantial resources into immigration security to rectify the flaws that those attacks revealed. Before 9/11, visa screening had almost no relationship to counterterrorism efforts. Because of U.S. officials’ near-exclusive focus on illegal immigration, neither consular officers abroad nor immigration officers at ports of entry received training to identify terrorists. The pre-9/11 vetting systems trusted unreliable and ineffective technological systems to catch terrorists, and intelligence agencies had virtually no engagement in disrupting terrorist travel. This allowed the 9/11 conspirators to violate immigration laws, submit applications lacking crucial information, use fraudulent or manipulated documents, obtain visas without consular interviews, and board U.S. airplanes dozens of times.
After 9/11, the focus of vetting changed immediately. The government created new agencies and improved methods to identify suspicious travelers. It mandated interviews for all visa applicants, created terrorist watch lists, deployed new technologies, created programs to train consular and customs officers to identify visa fraud, and spent billions of dollars on hiring additional immigration officers.
While the Trump administration released a report on foreign-born terrorists in January 2018, this analysis contains far more information about this phenomenon. It is the first to estimate whether vetting failures have increased or decreased since 9/11. It calculates the terrorism vetting failure rate—the rate at which immigration officials wrongly approve people to travel to the United States—and the risk of death to U.S. residents from terrorists admitted by those failures before and after 9/11. Lastly, it considers whether the vetting process itself caused the rate and risk changes that occurred since 9/11, and finds that the screening process has excluded more terrorists recently than in prior years.
Section I describes the vetting process, what went wrong on 9/11, and what government reforms were implemented to reduce the risk from foreign terrorists after that attack. Section II provides a quantification of the vetting failure rate before and after the 9/11 attacks. Section III considers the risk posed by those failures to the lives of U.S. residents by counting how many people were murdered in U.S. attacks by individuals who were radicalized prior to entry. Section IV considers whether the post-9/11 screening procedures caused the decline in vetting failures, how the post-9/11 failures occurred, and what the policy implications of this research are.
SECTION I: THE SCREENING PROCESS
Foreigners bear the burden to prove their eligibility for a visa under U.S. law.2 Any inability to support their claims results in a denial. Consular officers extensively vet the evidence that applicants provide. All visa applicants must submit a form with supporting documents to the U.S. Department of State.3 Among other information, this application must include any names by which the applicant has been known, addresses where they have lived, travel itinerary, means of financial support, age, gender, nationality, marital status, and date and place of birth.4 In the paper application portion of the process, they must support their identity claims with a photograph and other documentary evidence.
Congress has specified in statute that the relevant foreign government must also certify prison records, criminal background checks, marriage licenses, birth certificates, and military records.5 If certified copies of these records are unavailable or unreliable for any reason, consular officers may accept other documents that establish the same facts, but they are under no obligation to do so.6 Applicants must also present documents, such as bank statements and mortgages, to prove their claims about other matters, such as income sources or their likelihood to return home after a temporary stay.
Most nontourist visa applicants, such as guest workers, foreign students, and most immigrants, also need to submit proof of sponsorship. This proof consists of a notice provided by the U.S. Citizenship and Immigration Services (USCIS), an agency within the Department of Homeland Security (DHS). Schools, employers, and immigrants’ family members who meet various sponsorship requirements petition USCIS for foreign students, workers, or family relations. In these cases, USCIS checks both the sponsors and applicants against law enforcement and national security databases and records.7 Individual sponsors submit identity documents, fingerprints, and—in some cases—DNA test results to verify identities and relationships.8 Any concerns trigger a review under the Controlled Application Review and Resolution Program, which is an interagency review of the application.9 If the agency approves the petition, it sends the visa applicant a notice to apply for a visa from State.10
The Department of State consular officers then review applications for visas. If applicants appear to meet the requirements, a consular officer schedules them for interviews at the embassy or consulate. Interviews allow officers to evaluate the credibility of applicants and interrogate them regarding their reasons for seeking admission to the United States. At the embassy, all applicants between the ages of 14 and 79 submit 10 fingerprint scans.11 Consular officers check the application against the Consular Consolidated Database (CCD), which contains biometric and biographical information on the applicant (e.g., fingerprints, photographs, names, addresses, phone numbers, etc.).12 The database allows consular officers to see if there are any prior visa applications made by the individual and any comments by the prior adjudicator in those cases.13
As of 2016, the CCD contained more than 181 million records of visa applications dating back to 1998.14 It also links to DHS’s Automated Biometric Identification System known as IDENT, and the Federal Bureau of Investigation’s (FBI) Next Generation Identification system, each of which contain biometric and biographic records of terrorists and other criminals.15 The Department of State uses facial recognition software to search a gallery of photos of known or suspected terrorists from the FBI’s Terrorist Screening Center as well as CCD’s prior visa applications.16 In addition, State also operates the Consular Lookout and Support System (CLASS), an online database that includes more than 35 million people to whom it has denied visas or about whom other derogatory information exists.17 Any screener may also review the applicant’s public social media information.18
At any time, if the consular officers find grounds to believe that a person could be ineligible for terrorism reasons, they suspend the process and seek a Security Advisory Opinion (SAO), which launches an in-depth, multiagency review of the application by intelligence specialists.19 Consular officers may only approve an application subject to a Security Advisory Opinion if the person resolves all concerns to the satisfaction of the intelligence agencies.20 Refugees undergo a similar but more extensive vetting process. DHS, however, has primary responsibility for interviews and vetting abroad.21 Refugees must receive a referral, typically from the United Nations High Commissioner for Refugees or the U.S. embassy. They undergo multiple interrogations, and each factual claim is checked by security experts for consistency with prior statements and compatibility with known facts.22
Individuals who enter the United States from a Visa Waiver Program (VWP) country undergo a shorter vetting process. The VWP allows nationals from 38 countries to enter as temporary visitors without a visa or an interview at a consulate.23 Instead, they use the Electronic System for Travel Authorization (ESTA) system to apply online for preapproval.24 ESTA approval occurs after the DHS conducts a biographic background check that includes checking relevant terrorism databases. After they are approved by ESTA, individuals present their passports to board planes for the United States.
After the applicant receives a visa, refugee status, or ESTA approval and seeks to board a plane for the United States, DHS checks all flight manifests against terrorist watch lists.25 When foreigners arrive at a U.S. airport or at a land port of entry, they must undergo a primary inspection, which involves another brief round of questions about the purpose of the visits and a review of the identity documents.26 The officer at the port of entry again collects the person’s fingerprints and takes a digital photo of the person while rechecking criminal and terrorist databases.27 If anything raises suspicions, officials refer the visa holder to secondary screening. During secondary screening, specially trained officers conduct more thorough questioning and search the personal effects of the person.28 They may deny entry to any person that fails to cooperate or is suspected to have misrepresented their reason for entering.29
Pre-9/11 Vetting Deficiencies
The 9/11 terrorist attacks demonstrated major vulnerabilities in the visa screening process. The attackers planned their attacks prior to their arrival in the United States and yet they received temporary visas and admission to the country from April 1999 to August 2001.30 The security deficiencies that the attacks revealed were detailed in a devastating 241-page report on terrorist travel from the 9/11 Commission staff. Nearly all of the deficiencies that they identified were obvious and correctable, and this led to major revisions and improvements in the visa vetting process that would have prevented the attacks.
Visa security had almost no connection to stopping terrorism before 9/11 and counterterrorism agencies had little connection to visa security. Prior to the attacks, "no agency of the U.S. government" saw visa security "as a tool in the counterterrorism arsenal," according to the 9/11 Commission staff.31 Rather, a desire to facilitate lawful travel almost exclusively guided immigration policy throughout this time. Officers focused primarily on preventing illegal immigration by screening applicants to determine whether they were intending to work or reside illegally in the United States.32
This overriding pre-9/11 concern for illegal immigration prompted State to eliminate the visa interview for most people from countries where few visa applicants overstayed their visas. The 9/11 Commission staff found that "it was State Department policy that Saudi citizens, as a group, had overcome" the standard of proof for temporary visas regarding intent to live permanently in the United States.33 Therefore, they saw no other reason to interview Saudi applicants, including all of the Saudi 9/11 conspirators and 75 percent of all other visa applicants from that country.34 Staff at the U.S. embassy in Saudi Arabia justified the elimination of interviews and even the requirement to turn in the application in person as a security enhancement because it meant fewer people entered the embassy.35 The U.S. embassy in the United Arab Emirates (UAE), where other hijackers applied for visas, adopted a similar policy.36
Even when U.S. officers interviewed applicants, State provided no training on techniques to identify terrorists during those interviews.37 The U.S. consular officers in the UAE actually told the 9/11 Commission staff that they "were not familiar with al Qaeda."38 Application and document review was no better. Three of the 9/11 hijackers presented passports with an indicator of al Qaeda affiliation.39 As many as seven manipulated their passports to hide travel to Afghanistan.40 Consular officers failed to require Saudi applicants to resubmit incomplete applications—including several hijackers—or submit any documents to support claims about finances or addresses because, again, the staff believed that there was no reason to have them submit applications to begin with.41 Moreover, they had little technology and no training to detect terrorists’ fraudulent or manipulated documents during visa adjudications.42
The Department of State management considered rigorous review of applicants who presented no indications of an overstay risk as a waste of resources, and in a time when the visa workload grew more than one and a half times without a corresponding increase in funds, it had little choice in the matter.43 The department requested less funding to staff fewer positions, leading to a 20 percent reduction in Foreign Service staff from 1993 to 1996, even as the visa workload grew rapidly.44 This led to a chronic lack of oversight of consular officers who ignored obvious flaws in applications to expedite processing. Indeed, they approved all of the 9/11 hijackers’ visa applications with important information fields left blank.45 In the late 1990s, State flatly told its consular staff to schedule fewer interviews. Indeed, officers were even "discouraged from using [the standard of proof provisions in the law] to deny a visa to an applicant suspected of being a terrorist," being told to rely exclusively on State’s terrorism database known as TIPOFF.46 For these reasons, only two hijackers were interviewed when they applied for visas.47
In addition to no counterterrorism training, State had no uniform vetting procedures of any kind before 9/11. Individual embassies or consulates created procedures on their own without access to training and intelligence from around the world. Indeed, consular officers at many posts, including the German, Saudi, and UAE posts through which the 9/11 conspirators applied for visas, never wrote down critically important standards at all.48
The Immigration and Naturalization Service (INS), the predecessor agency to DHS’s immigration agencies, had even more problems with its screening than State. Like State, INS’s primary interest before 9/11 was facilitating lawful travel and its main concern was preventing illegal immigration. Drug interdiction was a distant secondary concern, and the agency apparently did not consider the threat of terrorism.49 As Congress poured money into Border Patrol, INS inspectors often relied upon temporary hires at ports of entry who lacked any substantive training.50 Permanent hires received no training at all about terrorist travel, no training regarding approaches to use for suspicious individuals referred to secondary screening, and only a half a day’s worth of instruction on conducting interviews at ports of entry.51
Even when INS officers conducted interviews, a congressional statute limited them to an average of just 45 seconds to determine each visitor’s eligibility for admission and to decide how long to authorize the interviewee to visit.52 This brevity led many inspectors to reduce their burdens by choosing to not look at the applicant’s customs form and instead leave this important task to customs personnel. This choice allowed one 9/11 hijacker to get away with using two completely different names on his customs form and his I-94 immigration entry form.53
INS failed to give inspectors at ports of entry any information about terrorist indicators in documents that could have enabled them to recognize anomalies that existed in some of the 9/11 hijackers’ passports.54 At least 2, and possibly as many as 11, of the attackers used manipulated or fraudulent documents to obtain their visas.55 INS also provided no training on how and when to use its law enforcement databases.56 Only 1 of the 26 inspectors who interviewed the 9/11 hijackers had even heard of State’s TIPOFF terrorism database, the only immigration-related database.57
INS had no uniform vetting standards and no oversight to enforce other standards related to enforcement of immigration laws. Essentially, inspectors made up the procedures as they went along. Some inspectors saw the visitor’s inability to support himself financially as a mandatory basis to send someone to secondary screening and ultimately removal. Others did not. One primary inspector referred a 9/11 hijacker to secondary screening for this reason while the secondary screener admitted him.58 The same pattern played out again when ringleader Mohamed Atta told a screener that he was entering to attend flight school even though he lacked a student visa. The secondary screener admitted him despite a legal prohibition against doing so.59 Some inspectors required a full destination address, while hijacker Saeed al-Ghamdi simply wrote "Hotel Orlando FL" before being allowed admission.60
Before 9/11, INS and State assumed that counterterrorism was a function of the intelligence agencies and the FBI, yet no agency of the U.S. government undertook a comprehensive analysis of how terrorists exploit weaknesses in travel documents and international travel channels to commit deadly attacks.61 The Central Intelligence Agency (CIA) as a whole simply did not engage in any ongoing analysis of terrorist travel.62 The FBI investigated specific acts of terrorism or leads about terrorist suspects but never aggregated its information to inform State or the INS on what it learned about their movements or methods.
Because counterterrorism was not a major focus of operations at INS or State, INS inspectors’ security clearances were insufficient to handle classified material so the intelligence agencies routinely ignored the few requests that they made for information.63 Two months before the 9/11 attack, for example, INS met with the National Security Council, CIA, FBI, Secret Service, and Customs to discuss a potential threat from "Mideastern" terrorists, yet when the INS manager attempted to obtain security clearances to share the information with inspectors at ports of entry, they ignored her request.64 A similar problem existed for State, which since 1993 had attempted to have intelligence agencies submit terrorist information to it directly for its TIPOFF database through its Visa Viper Program, but intelligence agents believed that the program could compromise their sources and methods, so it was underutilized.65
Pre-9/11 Technological Deficiencies
America’s immigration officers labored with primitive technology and lacked access to integrated and automated systems prior to 9/11. Since 1987, State operated a terrorism watchlist system known as TIPOFF that it began sharing with INS in 1991.66 Before 9/11, consular officers relied almost exclusively on this tool to identify terrorists who were applying for visas. If the applicant’s name failed to appear in the database, the officer assumed that they were not a terrorist.
However, neither INS nor State had the ability or expertise to gather intelligence on terrorists. Furthermore, INS never aggregated its reports on deported or detained aliens in a useable and accessible fashion.67 Both agencies were almost wholly dependent on submissions from the FBI, CIA, and National Security Agency (NSA) to TIPOFF, none of which were fully cooperative with the initiative. Even as the CIA developed watchlists for immigration agencies in several foreign countries from 1997 to 2001, it failed to collect the information from these efforts or its investigations, nor did it engage with State in any other way to improve TIPOFF.68 While some INS officials never used the program, all of the 9/11 hijackers cleared TIPOFF during State visa screening.69 The CIA had already identified two of the hijackers as terrorism suspects in 1999, but failed to share their names with State until it was too late.70 Another was identified, but again was added after he had entered the United States for the final time.71
No one at the FBI or CIA was consciously attempting to mine its investigation data to identify the names of foreign persons affiliated with terrorism. The FBI and CIA only searched this information pursuant to a specific investigation, and they never automated the process of adding people charged with terrorism offenses. The FBI, the 9/11 Commission staff found, "did not provide written guidance to its employees on how to collect and disseminate information on terrorists’ identities for inclusion in watchlists."72 In 2001, the FBI, the federal government’s main law enforcement agency, provided the same number of TIPOFF entries as the Australian government.73
Despite its reliance on CLASS—the system containing TIPOFF terrorist names, entries of visa refusals, and other derogatory information about applicants—State had glaring inadequacies in its name-check systems. CLASS and CCD would only automatically notify the consular officer of a past visa refusal. It failed to automatically give them information about prior approvals and provided them no access to actual immigration records, including those from INS, about the applicant.74 When multiple hijackers reapplied for visas with new passports—to hide their travel patterns on their old ones from the INS inspectors—they claimed to have never applied for U.S. visas before, yet the system failed to alert consular officers to the fact that they not only had applied but currently possessed valid visas.75
As problematic was the total dependence on biographic information such as names, passport numbers, and birthdates. Without collecting biometric information (fingerprints) from applicants, State had no way to know whether they used aliases. Khalid Sheikh Mohammed, the 9/11 mastermind, was able to receive a visa in Saudi Arabia under a false name without even being in Saudi Arabia—and while being listed in TIPOFF.76 Likewise, although INS began to collect biometrics on people denied entry at the border under its IDENT system, it had no mandatory biometric entry collection. Because State had the same policy for visas, INS inspectors at ports of entry had no way of verifying that the person standing in front of them was the same person who applied for a visa. Indeed, they could not even access State’s visa photograph.77 IDENT systems collected only two fingerprints from individuals turned away at the port—such as would-be hijacker Mohammed al Qahtani—so even for several years after 9/11 it could not run biometric entries against the FBI’s database that used a 10-fingerprint platform.78
Substantial investments in new technology failed to integrate terrorist information in a way such that INS officers could easily access it.79 On numerous occasions during this time, INS granted terrorists admission, status extensions, and other benefits even as the FBI and CIA suspected their involvement in terrorism and conducted investigations or even prosecutions of them.80 INS even approved two of the 9/11 hijackers’ applications to attend flight school in 2002 after the attacks.81 The focus during the mid-1990s was moving border agents away from manual typewriters and inspectors from paper-based watchlists (which they had 45 seconds to consult).82 Other technology to detect manipulation, such as black lights, was often broken. One inspector told the 9/11 Commission staff that he actually had to buy his own.83 While INS inspectors accessed INS databases and the IDENT biometric system, none of the inspectors who admitted the hijackers used them.84
Despite almost zero terrorism training or focus, consular officers initially denied 488 people visas on "terrorism grounds" from 1992 to 2001.85 Moreover, consular officers and INS inspectors managed to refuse visas to five coconspirators in the 9/11 attacks and denied entry at a U.S. airport to another. The five visa refusals all occurred because the terrorists failed to meet their burden of proof and consular officers deemed their travel illegitimate, believing that they would likely overstay their visa.86 An Orlando INS inspector referred 9/11 conspirator Mohammed al Qahtani to secondary screening because he made her feel "uneasy" and was the first Saudi that she had met who spoke no English.87 The secondary inspector denied him entry because al Qahtani became extremely irritated, refused to answer questions under oath, had no return ticket, and refused to explain where and for how long he would stay in the United States.88 Saudi-based consular officers might have noticed these behaviors in him and other hijackers—had they interviewed them.
Post-9/11 Vetting Enhancements
After 9/11, Congress overhauled the entire vetting system. It is impossible to detail all of the reforms, but Congress and the administration replaced nearly the entire pre-9/11 security system and methods. Consular staff had to undergo retraining to focus on security issues.89 The State Department created four mandatory training classes on terrorism-related issues, including document and visa fraud, handling counterterrorism information, and interviewing visa applicants run by the CIA.90 In the immediate aftermath of 9/11, State established more uniform vetting processes, issuing more than 80 security standard operating procedures to guarantee that officers review applications for signs of fraud, deception, or terrorism connections.91
Before applying for visas, for example, most of the 9/11 hijackers obtained new passports—just days old when they applied—to hide their travel patterns, yet the new passports triggered no heightened scrutiny as they would today.92 State brought in counterterrorism experts to evaluate visa interviews and reversed its policy of discouraging visa interviews.93 By 2004, consular officers interviewed nearly all new applicants for visas.94 State instituted ongoing retraining in light of new developments.95 To cope with the increased workload, State nearly doubled the number of consular officers from 1,037 in 2002 to 1,883 in 2014.96
The intelligence community finally awoke to the need to engage with the immigration agencies and Congress improved interagency communication, creating the National Counterterrorism Center (NCTC) under the newly created Director of National Intelligence in 2004. As part of its new Terrorist Screening Center, the FBI took over the primary responsibility for the terrorist watchlist from State, implementing the Terrorist Screening Database (TSDB) in 2004.97 All intelligence agencies must now submit terrorism suspects to the list. As of June 2016, it contained roughly a million.98 TIPOFF contained just 60,000 names on the morning of September 11, 2001.99 State’s CLASS now automatically incorporates these data.100 CLASS itself contains 35 million records on visa refusals, criminals, and others—up from 10 million in 2001.101 State also created secure channels to send highly classified reports to consular officers who need them.102 In 2013, it partnered with the National Counterterrorism Center on the Kingfisher Expansion, which uses classified information from all federal holdings to screen for terrorism concerns.103
The U.S. immigration system has far more data from around the world fed into it today than before 9/11. In 2007, DHS and State began to incorporate fingerprints and other data from the Department of Defense, obtained during the occupations of Iraq and Afghanistan, into their background checks.104 In 2010, DHS and State entered into agreements to exchange biometric and biographic data about visa applicants with Australia, Canada, New Zealand, and the United Kingdom.105 Under the VWP, 38 countries must now promptly share data on lost or stolen passports and exchange intelligence regarding known or suspected terrorists.106 In 2011, the United States and the European Union agreed to share extensive passenger information, including contacts, credit cards, and baggage information.107
The State Department also began to crosscheck new watchlist entries against existing visa holders to allow them to revoke a visa after its issuance. If this had been in place before 9/11, it could have tipped off the department to multiple hijackers.108 The agency also digitalized its photo database, which it had only created in February 2001, to allow for facial recognition searches.109 Before 9/11, many immigration records existed only on paper and officers could not easily search them. In 2004, State transformed the paper-based security vetting into an electronic "interoperable network" to share information between agencies.110 In 2010, State created an online nonimmigrant visa application, allowing easier pre-interview electronic vetting.111 At the same time, State fulfilled the 9/11 Commission’s recommendation to introduce biometric indicators—namely photographs and fingerprints—into all new visas.112
In 2002, Congress created the Department of Homeland Security in part to replace INS and to facilitate better communication between various aspects of the immigration system and the intelligence agencies. The new agency implemented another 9/11 Commission recommendation with its U.S. Visitor and Immigrant Status Indicator Technology (US-VISIT) system, which collects biometrics upon arrival in the United States and allows for instantaneous comparison to the biometric visa information collected by State.113 Imposters posing as the correct recipient carried out nearly 80 percent of visa fraud, so these improvements were critical security enhancements.114
The Department of Homeland Security created Visa Security Units to support State visa screening. It has deployed these units at 26 visa-issuing posts, and in 2010 they reviewed 815,000 visa applications, leading to 1,300 denials.115 Before 9/11, airlines could voluntarily provide flight manifest information, but even when they chose to, the information was incomplete and inconsistent.116 Now DHS prescreens all passengers on all U.S. flights—domestic and international—against watchlists with its Secure Flight system, which would have identified the three 9/11 hijackers who were added to TIPOFF after their entries.117
The Department of Homeland Security also created the Electronic System for Travel Authorization to require preapproval for VWP travelers who enter the United States without visas. This system became operational for all VWP countries in 2009.118 By 2006, all VWP countries had to issue only machine-readable passports that incorporate a biometric identifier.119 By 2016, all visitors had to use e-Passports, which contain an electronic chip with all biographic and biometric data as well as their travel history.120
The most important change was that immigration officials began to take terrorism seriously. Before 9/11, immigration officials considered security a minor aspect of their jobs, primarily viewing visa issuance as a customer service endeavor. In 2002, State admitted that in reacting to increased demand in the 1980s for temporary visas, "consular managers, encouraged by Washington, have addressed the lack of officers with a variety of approaches, often referred to under the term ‘customer service.’"121 More than anything, 9/11 changed visa security culture and made every officer aware that security was the top priority. These changes would have prevented the 9/11 attack and likely did prevent potential attacks after 9/11.
SECTION II: TERRORIST INFILTRATIONS
Missing from all this is an estimate of the rate at which consular officials still approve terrorist visa applications after 9/11. Even so, one of President Trump’s first actions was to sign Executive Order 13769, titled in part, "Protecting the Nation from Foreign Terrorist Entry into the United States."122 When a federal judge blocked this order, Trump signed a successor of the same name, Executive Order 13780.123 Both orders suspended all entries of refugees for at least 120 days and nationals of several Middle Eastern and North African countries for at least 90 days.
The stated purpose of these suspensions was to allow the DHS time to study the visa vetting process.124 As evidence that the screening process is inadequate, the order claimed that some people "who have entered the United States through our immigration system have proved to be threats to our national security," and specifically, "Since 2001, hundreds of persons born abroad have been convicted of terrorism-related crimes in the United States."125 But simply because someone was born abroad does not mean that he or she entered the United States as a result of a vetting failure.
Each order required DHS to issue a report within 30 days to identify "whether, and if so what, additional information will be needed from each foreign country to adjudicate an application by a national of that country for a visa, admission, or other benefit under the [Immigration and Naturalization Act] (adjudications) in order to determine that the individual is not a security or public-safety threat."126 No official report was ever filed, but a draft DHS intelligence assessment was leaked roughly 30 days after the first order was signed.127 In the leaked report, DHS reviewed 88 foreign-born, U.S.-based persons who were "inspired by" a foreign terrorist organization and who participated in "terrorism-related activity" from March 2011 through December 2016.
The DHS draft intelligence assessment concluded that "most foreign-born, US-based violent extremists likely radicalized several years after their entry into the United States."128 It based its conclusion on two factors: half of the extremists in its dataset were children when they entered the United States, and the majority of the extremists resided in the United States for a decade or more before their indictment or death (though these categories may overlap). Despite this conclusion, the president replaced the second order with yet another in September 2017, banning immigration from Chad, Iran, Libya, Syria, Somalia, Yemen, and North Korea, while barring certain government officials from Venezuela.129
In January 2018, the administration released a joint report from the Department of Homeland Security and the Department of Justice (DHS-DOJ) about foreign-born terrorists.130 It only reported the citizenship status—U.S.-born, naturalized, or noncitizen—of "international terrorism-related" convicts. It failed to include domestic offenders or offenders who were killed in terrorist attacks. Moreover, it reported that "DHS and DOJ lack unclassified, aggregated statistical information pertaining to the timing of individual radicalization," providing little new useful information about the adequacy of terrorism vetting.131
Sections II and III of this paper expand upon the DHS intelligence assessment in six significant respects. First, they enlarge the period of analysis to October 1986 through October 2017—the month after the president signed the final executive order—evaluating 604 total offenders. Second, they estimate the number of vetting failures. Third, they identify the status or visa involved in each of the vetting failure cases. Fourth, they calculate the vetting failure rate for each admission category. Fifth, they provide the risk of death from terrorism as a result of vetting failures compared to the risk of death from other causes of terrorism. Sixth, for each of these results, they estimate the changes over time, comparing the results in the most recent 15-year period from 2002 to 2016 to the 15-year period from 1987 to 2001 leading up to 9/11.
Methodology and Sources
This analysis relies on publicly available information in court documents, government releases, and news reports to identify nationalities and years of entry.132 For sources for the list of terrorism offenders, the 2017 draft DHS intelligence assessment referenced above relied on a list of unsealed international terrorism and terrorism-related convictions from the National Security Division of DOJ as well as unnamed "academic and government" sources.133 In addition to the same DOJ conviction list, this paper includes individuals whose terrorism convictions DOJ has publicized on its website from 2015 to October 2017—just after the president’s most recent order.
As with the DHS analysis, this analysis supplements the DOJ sources with several leading academic sources, including George Washington University’s Program on Extremism (GW), and the New America Foundation’s International Security Program (NAF).134 The DOJ has not released a list of terrorism convictions prior to 9/11, and neither the NAF nor GW data extend before 2001. However, a 2016 Cato Institute report provides an exhaustive list of foreign-born terrorists who plotted or conducted an attack in the United States, and the 9/11 Commission’s staff report on terrorist travel provides several additional offenders who did not plot an attack.135 In addition, the Global Terrorism Database (GTD) maintained by the National Consortium for the Study of Terrorism and Responses to Terrorism at the University of Maryland, College Park, provides a list of terrorist attacks by both foreign and U.S.-born offenders.136
The Global Terrorism Database also provides the total number of terrorism deaths each year, and the number of deaths in each attack. To identify the risk of death as a result of a vetting failure, this analysis apportions deaths from terrorist attacks based on whether the attacker entered the United States as a result of a vetting failure. It does not include the deaths of the terrorists themselves. If an attacker had coconspirators, each attacker is credited with the same portion of the deaths from the attack as their share in the conspiracy. For example, the five 9/11 conspirators hijacked and crashed a plane into the Pentagon, killing 189 people, including themselves. This analysis counts this attack as killing 184 people, crediting each attacker with 36.8 deaths.
Following Cato’s 2016 report’s methodology, foreigners are credited with all deaths in an attack in which a U.S.-born citizen participated. For example, the two San Bernardino shooters—Tashfeen Malik, a Pakistani national, and Syed Rizwan Farook, a U.S.-born citizen—killed 14 people. Malik received credit for all 14 deaths for calculating the risk of death, though Farook is still included as a "lethal attacker" in statistics showing the place of birth of such attackers. This decision intentionally overstates the risk from foreign attackers.
Identifying Terrorism Offenders
This analysis concentrates on foreign entries of the United States primarily during the period from October 1, 2001, to September 30, 2016, which corresponds with fiscal year (FY) 2002 to FY 2016. It includes terrorism convictions or attacks up to October 2017, as explained below, but all entries occurred in the FY 2002 to FY 2016 period. These years cover the time immediately following the 9/11 terrorist attacks as the federal government moved to improve its immigration screening. It compares this 15-year period to the 15-year period leading up to the attacks, from October 1, 1986 to September 30, 2001 (FY 1987 to FY 2001). It counts terrorism offenders convicted or killed, identifies their nationalities, and, if born abroad, their ages at entry and their years and modes of entry to the United States. It also counts six offenders charged with killing people in attacks in 2016 and 2017.
Nationalities were identified in all but one case, and in that case the government and the defendant herself appeared to assume the United States as her birthplace, so this analysis will also.137 In a few cases, a specific entry year was unavailable, but a date by which the person must have entered was available. Those who naturalized, for example, must generally have resided in the United States for at least five years before receiving citizenship. Others had business, employment, or school records that provided the latest possible date for entry.138 In lieu of a precise date, this analysis uses the first year during which the person had to have been in the country. Thus, if someone is known to have been in the country in 2012, but it is uncertain whether the person was in the country before then, this analysis assumes 2012 as the entry date. Because this analysis assumes anyone who committed an offense within 10 years of entry was a vetting failure, this dating method biases the analysis in favor of finding a vetting error. In two cases, the year of entry and the category of entry were unknown. This analysis assumes that these people entered legally the year before their offense.
Altogether since 1987, 521 terrorism offenders were convicted of a terrorism offense, 77 were killed while committing such an offense in the United States or abroad, and 6 were charged with killing someone in an attack but have not yet been convicted. "Terrorism offense" is defined as any DOJ Category I terrorism conviction, meaning cases that are "directly related to international terrorism."139 To avoid missing any serious offenders whom the government charged under nonterrorism statutes, this analysis broadens Category I to include any DOJ Category II offense that involved a conspiracy to commit a Category I offense as well as any Category II violent crime or conspiracy to commit a violent crime.140 Terrorism offenses prosecuted under state law rely on the Global Terrorism Center’s definition of terrorism: violent acts "aimed at attaining a political, economic, religious, or social goal" through intimidation of a "larger audience."141
Appendix A provides a list of all federal terrorism offenses included in this analysis. The most common offenses were material support to terrorists or material support to a designated foreign terrorist organization (FTO), with a combined 249 convictions. There were another 30 conspiracy offenses, primarily conspiracies to support terrorism or a foreign terrorist organization. The only other offenses in double digits were the use, or attempted use, of weapons of mass destruction (37 convictions); murder or attempted murder of government employees (26 convictions); conspiracy to murder, kidnap, maim, or damage property overseas (23 convictions); and possession of a missile designed to destroy aircraft (11 convictions). Note that an offender may have been convicted of multiple such offenses, so the number of convictions is larger than the number of offenders. Another 77 people were killed during the commission of a terrorism offense. These deaths primarily include people who allegedly went overseas to fight for terrorist organizations.
Under its Category II designation, DOJ counts a very large number of nonterrorism offenses as "terrorism-related" convictions. Of its 627 individuals, 45 percent (279) were incarcerated solely for nonterrorism offenses. DOJ labels them terrorism-related because the conviction was the result of a terrorism investigation. NAF and GW also include an additional 14 convictions of persons whose convictions were for nonterrorism offenses. Appendix A also provides a list of every offense that the DOJ, GW, or NAF includes that this report excludes, counting only those convictions where the government did not also convict the defendant of a terrorism offense. These include 63 convictions for making false statements to the government; 64 for identification, visa, or passport fraud; 50 for money laundering; 40 for immigration violations; 29 for various forms of financial fraud; and 16 firearm offenses. Others include Social Security fraud, drugs, and child pornography. Some of these nonterrorism offenders had multiple nonterrorism convictions.
Figure 1 categorizes the four broad types of offenders convicted of terrorism-related offenses, including all of DOJ’s Category I and Category II offenses as well as all convicted NAF and GW offenders. Terrorists who plotted or carried out a U.S. attack made up only 22 percent of ‘terrorism-related’ offenders from October 2001 to October 2017 ("U.S. plots"). Nearly half of all cases involved nonterrorism offenders (37 percent) or individuals extradited or brought into the United States by the government during a sting operation (12 percent). The U.S.-based terrorism offenders made up barely half of all terrorism-related offenders during this time.
Focusing only on those convicted of terrorism offenses could exclude from the analysis some undesirable people who may have radicalized but who were never convicted of a terrorism offense. For example, an analysis could include immigrants who had their visas revoked on terrorism grounds without a prosecution for terrorism. Focusing solely on terrorism convictions, however, allows for comparison between U.S.-born and foreign-born offenders and directs the attention to individuals whose cases were serious enough to involve a terrorism prosecution, which are also the focus of the president’s executive order.142
Defining Vetting Failures
A terrorism vetting failure occurs when a foreigner is granted entry to the United States who had, at the time of approval, terrorist associations or sympathies and later went on to commit any kind of terrorism offense, including support for terrorist groups abroad. Concerning the information unidentified in a vetting error, "information" is defined as broadly as possible to include private communications or later-discovered private intentions. This measure only captures the inability of U.S. officials to identify this information and not whether consular officers should have been able to gather it. This analysis starts with the assumption that unless other evidence comes to light, anyone who commits a terrorist offense within 10 years of entry into the United States initially entered the country with the intention to commit such an act.
The vetting failure rate is defined as the number of visa approvals and lawful entries without visas per failure. This rate depends on three factors: the number of nonterrorist applicants, the number of terrorist applicants, and the efficacy of the terrorist screening. The visa vetting failure rate could decline if the number of nonterrorist applicants increases, the number of terrorist applicants decreases, or the efficacy of the test increases. Section IV addresses the number of terrorist applicants and the efficacy of the terrorism test.
This analysis focuses only on the first visa that successful applicants receive and their subsequent admission. Although vetting also occurs after foreigners have entered the United States—such as when they apply for citizenship or adjust their status to a different classification—the initial failure is what puts U.S. lives and property at danger. The initial approval often allows for subsequent ones even if they temporarily leave the United States.
If offenders did leave the United States and received new visas overseas, this analysis only counts their second approval if they had left the country for at least five years and if they concealed their earlier entries in some way (as occurred twice). For example, although Khalid Sheikh Mohammed lived in the United States from 1983 to 1986 (a period outside the scope of this study), he used an alias to receive a visa in 2001.143 Ali Saleh Kahlah al-Marri also lived in the United States in the 1980s, but he lied about it when he reapplied for a visa in 2000.144
Furthermore, this analysis treats visa issuance and admission as two parts of a single vetting process. A vetting failure occurs if an offender evaded either portion of the vetting process. Thus, although Khalid Sheikh Mohammed never used his visa, his approval counts as a vetting failure.145 Similarly, while an airport inspector denied Mohammed al Qahtani entry at an airport, the fact that he received a visa and approval to travel to the United States is a security failure.146 Richard Reid is also included, although his attempted attack occurred on a U.S.-bound airplane and not after his entry to the United States.147
Identifying Vetting Failures
Vetting failure cannot explain the presence of terrorists in the United States in three situations: individuals who were born in the United States, those who entered illegally, or those who received authorization to travel to the United States only because U.S. law enforcement wanted them to enter the country in order to arrest or prosecute them. These would include extradited offenders or foreign suspects that the FBI enticed to enter U.S. jurisdiction in order to make arrests as part of a sting operation. Vetting failure is also an unlikely explanation for people who entered as juveniles. Consular officers did not fail at vetting applicants when the young children they approved for a visa grow up and become terrorists.
To define "child," there are plausible arguments for using various ages younger than 18. Consular officers generally only interview visa applicants if they are 14 or older.148 However, the government has never charged an individual under the age of 17 with terrorism.149 DHS’s 2017 intelligence assessment assumed that there are no vetting failures for individuals under the age of 16, and the State Department appeared to adopt a similar view immediately after 9/11 when it suspended visa issuances for 20 days for men in several countries between the ages of 16 and 45.150 For these last two reasons, this analysis will adopt the presumption that if people entered when they were 15 years old or younger, their eventual terrorist acts resulted from failed assimilation and not from a visa vetting failure.
For offenders who entered as adults, this analysis reviews individuals’ case histories to identify whether there were indications of radicalization prior to their entry to the United States. If evidence is contradictory, it relies on government sources. For example, Quazi Nafis claimed that he did not intend to commit an offense when he entered the United States and that the FBI entrapped him, but the government asserted that he entered with the intention of committing a terrorist attack, so this analysis counts him as a vetting failure.151
Additionally, this analysis follows the DHS assessment in considering a short residency prior to indictment or death in a terrorist act as an indication of radicalization prior to entry. The longest period between entry and charge in a case involving a post-9/11 entry, where the government had any evidence of radicalization prior to entry, was seven years. The Department of Homeland Security considered more than a 10-year residency as an indication that radicalization occurred after entry. This analysis adopts that assumption, but further assumes that less than a 10-year residency is an indication of radicalization before entry.
Thus, if an offender’s indictment or death occurred within a decade after his or her initial arrival in the United States, this analysis adopts the presumption that the person’s actions were the result of a vetting failure, unless evidence emerged to the contrary (see below). The goal of this presumption is to count anyone who plausibly could have intended to commit a terrorism offense at the time of entry, even if the government never found evidence of such an intent. This presumption resulted in the inclusion of an additional 14 offenders as vetting failures who entered before 9/11, and one such offender who entered after 9/11.
Identifying Non-Vetting Failures
Following DHS, this analysis does not consider anyone who entered before the age of 16 or who lived in the United States for at least a decade before their charge to be a vetting failure. This presumption resulted in the exclusion of 75 offenders who entered before 9/11 and 2 offenders who entered after 9/11. A longer residency presumption of, for example, 15 years could potentially increase the number of vetting failures, but only for the pre-9/11 period. The evidence indicates that the two post-9/11 entrants who committed their offenses after 10 years of U.S. residency radicalized after their entry and would be excluded regardless. Gufran Ahmed Kauser Mohammed, who committed his offense in 2013, came to the United States in 2003 at the age of 20 and radicalized after he moved to Saudi Arabia in 2011.152 Tamerlan Tsarnaev, one of the 2013 Boston Marathon bombers who immigrated to the United States as a 16-year-old in 2003, radicalized around the time of his 2012 trip to Russia.153
Since 9/11, only 25 people entered the United States for the first time after the age of 16 and went on to commit a terrorism offense within 10 years of entry. Of these, evidence indicates that 12 radicalized after their arrival. Five post-entry radicalizations involved people who entered as older teenagers. Yonathan Melaku, who shot at the Pentagon in 2010, converted to Islam after he immigrated to the United States as a 16-year-old in 2005.154 The FBI concluded that Omar Faraj Saeed Al Hardan, a Palestinian born in Iraq who lived in Texas for seven years from the age of 17, "was radicalized after he arrived in 2009."155 Ulugbek Kodirov, according to the prosecutor, became "radicalized by misinformation and propaganda on the Internet" after his 2008 arrival as a 19-year-old.156
Abdul Razak Artan, a Somali child of an asylee who entered as a 16-year-old, "self-radicalized" online inside the United States, according to Homeland Security Secretary Jeh C. Johnson, House Homeland Security Committee Chairman Michael McCaul (R-TX), and Rep. Adam Schiff (D-CA), the ranking member of the House Intelligence Committee—all of whom received confidential FBI briefings on his case.157 According to court filings, Akhror Saidakhmetov, another child of an asylee who also entered as a 16-year-old, radicalized online in response to ISIS propaganda and sought to travel to Syria.158
Five offenders entered after 9/11 while in their 20s, and then radicalized. Abror Habibov, the Uzbek man who financed Saidakhmetov’s travel, entered as a 21-year-old in 2006 or possibly earlier on a temporary visa and lived in the United States for nine or more years before his offense.159 Habibov married a non-Muslim wife in 2008 and, according to her, he never practiced Islam. However, after he abandoned her in 2010, he began to support the Islamic State, and then divorced her in 2013.160 Saidakhmetov’s Uzbek traveling companion, Abdurasul Juraboev, entered in 2011 as a 21-year-old after winning the green card lottery, and then radicalized online in response to ISIS propaganda.161 Another Uzbek man, Sayfullo Saipov, who also won the green card lottery in 2010 as a 22-year-old, lived in the United States for seven years before killing eight people with a truck in 2017. Investigators concluded that he "radicalized online after he came to the United States."162
According to prosecutors, Agron Hasbajrami, a 2008 green card lottery winner from Albania, entered as a 24-year-old in order to "pursue a career as an architect."163 At his sentencing, it was "undisputed that when Hasbajrami immigrated to the United States he did not do so with the intent of committing any crimes."164 Ahmed Mohamud, a Somali national who won a greencard through the diversity visa lottery in 2004 at the age of 28, ended up playing what the government described as a "minimal role" in a 2011 scheme to send money to Al-Shabaab, the Somali terrorist organization.165 The federal judge described his history as "law-abiding and productive" prior to meeting the conspirators after he moved to St. Louis several years after his arrival in the United States.166
Two of these offenders entered the United States while in their 30s. Amina Mohamud Esse, a Somali refugee who entered in 2009, does not appear to have ever truly radicalized. She contributed money to Somalia, but upon discovering that the money went to Al-Shabaab, she told the conspirators that she wanted to stop.167 They threatened her and she briefly continued to send them money but then decided to stop, at which point her husband expelled her from their house. She ultimately pleaded guilty to material support for a terrorist organization, and in an unprecedented decision, the judge—with the support of the prosecutor—gave her probation. The oldest entrant was Adnan Fazeli, an Iranian. Fazeli converted from Shia to Wahhabi Islam after his arrival and ultimately left the United States to fight for the Islamic State, where he died in 2016—more than seven years after his arrival in the United States.168 The other 13 offenders who entered after 9/11 are considered vetting failures.
This analysis excludes four offenders who entered before 9/11 and committed offenses within their first 10 years in the United States. Khaleel Ahmed came to the United States in 1998 as a 17-year-old who later, according to prosecutors, radicalized in the United States in response to the U.S. invasion of Iraq in 2003, being arrested in 2007, nine years after entry.169 Similarly, Shahawar Matin Siraj entered legally in 1999 from Pakistan as a 17-year-old and later applied for asylum. His parents are moderate Ismailis, and an uncle in the United States apparently converted him to Sunni Islam after which he radicalized on his own before his 2004 arrest. In a bizarre case, Patrick Abraham, who entered the United States from Haiti nine years before his charge, was not Muslim, but according to the government a friend whom he had met in the United States recruited him into a plot to defraud a federal informant by pretending to be part of al Qaeda.170 The federal judge described him at sentencing as easily manipulated into the scheme.171 In an equally bizarre case, German tourist Karen Paulson fell in love with a member of the Republic of Texas, a U.S. militia group purporting to establish an independent country in Texas, and wound up participating in a hostage-taking plot.172 Paulson was not a Texas nationalist before her arrival in the United States.
Vetting Failure Rates
Figure 2 groups vetting failures by the period of entry of the offender. As it shows, vetting failures have become much less frequent since 9/11. Four times as many vetting failures occurred in the 15 years leading up to the attacks than in the 15 years that followed. Before the attacks, 52 offenders who radicalized prior to entry were convicted of terrorism or killed during a terrorism offense, compared to just 13 offenders after 9/11. Appendix B lists each vetting failure with their biographical details—for example, dates of arrival, age at arrival, and nationality—as well as all terrorism offenders along with their details.
From FY 2002 to FY 2016, consular officers issued 115 million visas at foreign posts abroad, and DHS authorized status for 1.2 million refugees and asylees and permitted 262 million entries for people from VWP countries without visas.173 Of these 373 million total approvals, there were 13 terrorism offenders (Table 1). During the 15-year period from FY 1987 to FY 2001, there were 103 million visa approvals and 1.7 million refugees and asylees, as well as 142 million VWP approvals. Among these 247 million total approvals, there were 52 terrorism offenders. Thus, the terrorism vetting failure rate has fallen 84 percent since 9/11—from 1 failure in 4.8 million vetting approvals prior to 9/11 to 1 failure in 29.1 million after 9/11.
To put this rate in context, the U.S. government granted vetting approvals for a nonterrorist population roughly equal to the combined populations of America’s 14 largest cities for each terrorism offender it wrongfully approved over the last 15 years.174 It is also important to note that these figures exclude hundreds of millions of entries by Canadian and Mexican legal border crossers, which the government does not systematically track.175
As seen in Figure 3, about half of the 52 vetting errors from FY 1987 to FY 2016 occurred during the three years before 9/11. Of those errors, 21 involved conspirators in the 9/11 attacks. Even excluding the 9/11 conspirators, however, both the number and rate of failures have declined significantly since 2002. After 9/11, a majority of the 15 years saw no vetting failures at all, while only 2 of the 15 years before 9/11 saw no failures. Almost three-quarters of the post-9/11 failures were clustered in the years 2007 through 2009. In only one year after 9/11 were vetting failures more frequent than 1 failure in 10 million approvals, while the error rate rose above that level 11 times before 9/11.
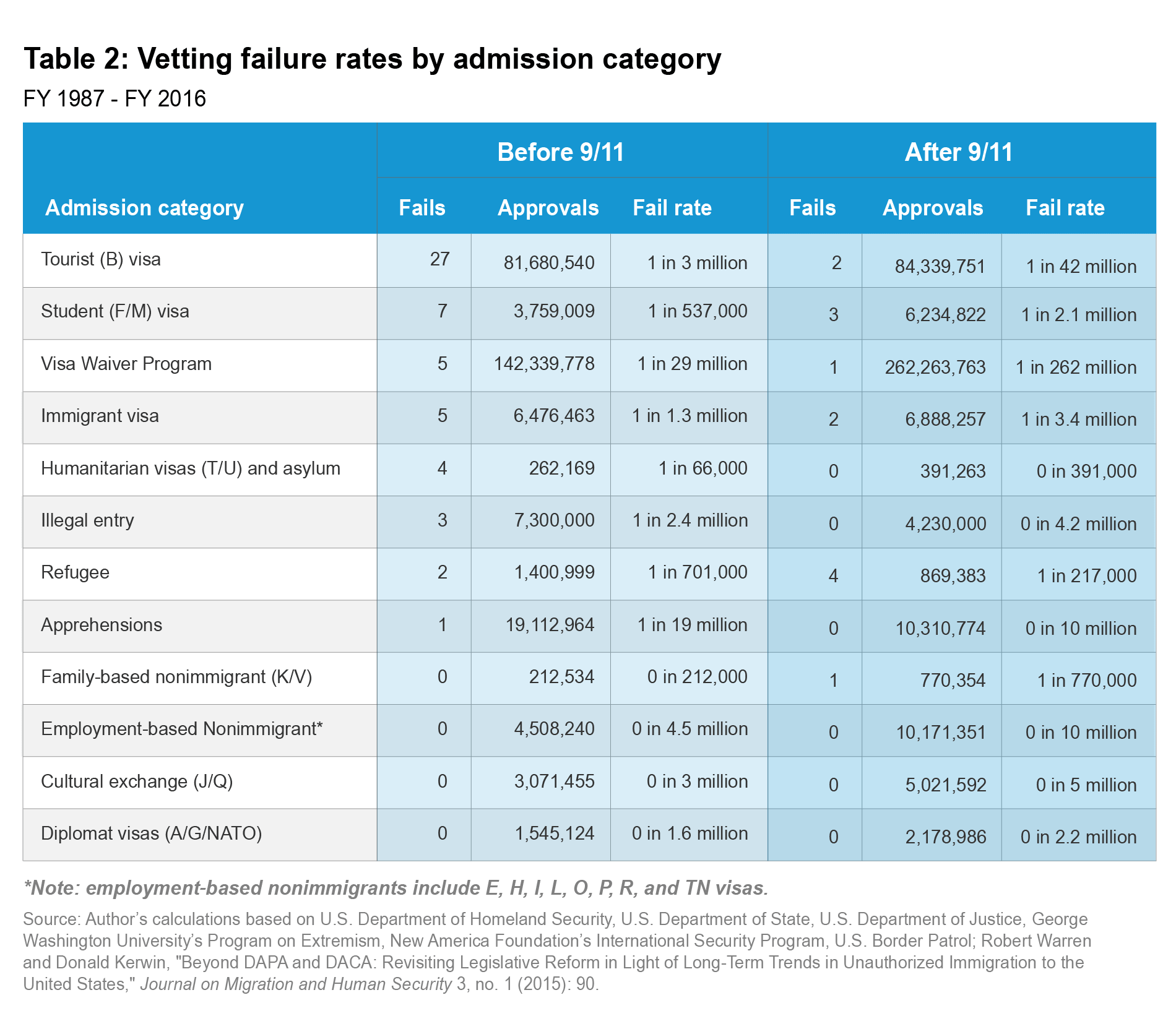
As Table 2 shows, the vetting failure rate decreased for most admission categories as well. The most dramatic decrease occurred for tourist (B) visas and the VWP, where the failure rates dropped 93 and 89 percent, respectively. The student (F) visa failure rate fell 74 percent. The immigrant visa vetting failure rate for people coming to live permanently in the United States declined 62 percent, from 1 in 1.3 million to 1 in 3.4 million. Before 9/11, asylum claims allowed two terrorists to enter, while none did so after 9/11. Only two categories saw vetting failure rate increases since 9/11: refugees and family-based nonimmigrants.
While not included in the "vetting failures" in Table 1, Table 2 includes two categories of illegal border crossers: those who made it across the border and those whom Border Patrol apprehended. Before 9/11, Border Patrol caught and released one terrorism offender who radicalized prior to entry (as was a common practice for non–asylum seekers at the time), and it failed to apprehend three others.176 Neither situation has happened since 9/11. Several categories have not had a single visa vetting failure at any time in the past three decades: temporary workers of all skill levels, cultural exchange visitors, and diplomats from all countries.
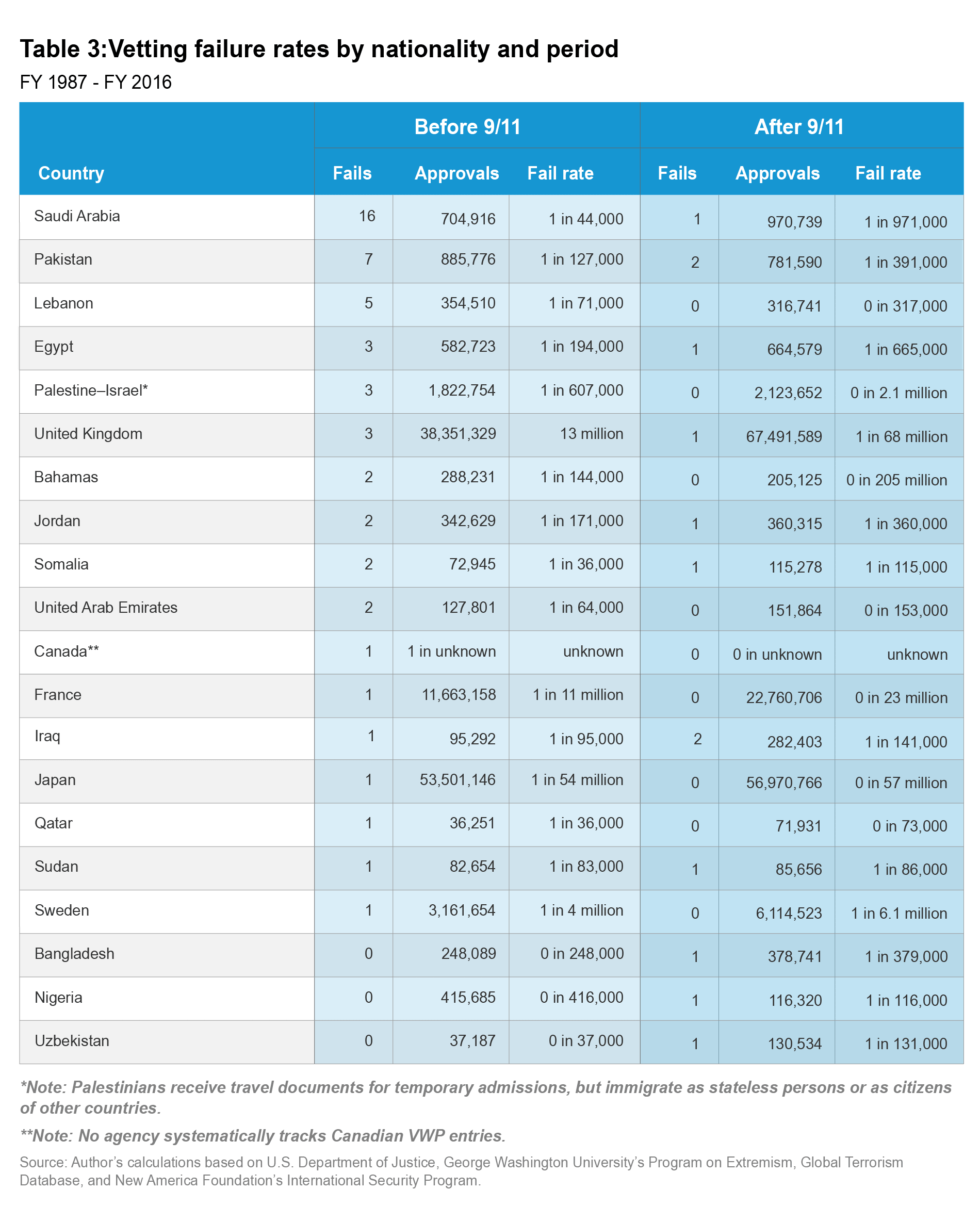
Table 3 provides the vetting failure rates for the 20 nationalities that had at least one vetting failure since 1987. Each represents the nationality under which the person first entered the United States, not necessarily the person’s place of birth (although place of birth is relevant for all immigrant visa applicants). Vetting failure rates declined for each nationality that had a failure before 9/11. Prior to 2002, 10 nationalities had multiple failures, including 6 with three or more failures. After 9/11, there were only two nationalities with multiple failures and none with three. Only one of the eight nationalities singled out by the president’s travel ban—Chad, Iran, Libya, North Korea, Syria, Somalia, Venezuela, and Yemen—had any failures in either period (Somalia). During this time, the other travel ban countries saw 5.5 million visa issuances and refugee admissions.
Ten of the 17 nationalities that saw at least one vetting failure before 9/11 saw none at all after 9/11, and 3 others had a vetting failure for the first time (Table 3). Moreover, the four nationalities with the most failures before 9/11 produced a combined 31 vetting failures. After 9/11, those four countries produced only a combined four failures. Most dramatically, Saudi Arabia had just 1 after the attacks, while it had 16 before them. These facts highlight the difficulty of predicting future terrorist infiltrations and the futility of designing a ban to stop them. They also highlight the capability of the U.S. government to suppress failures without nationality bans.
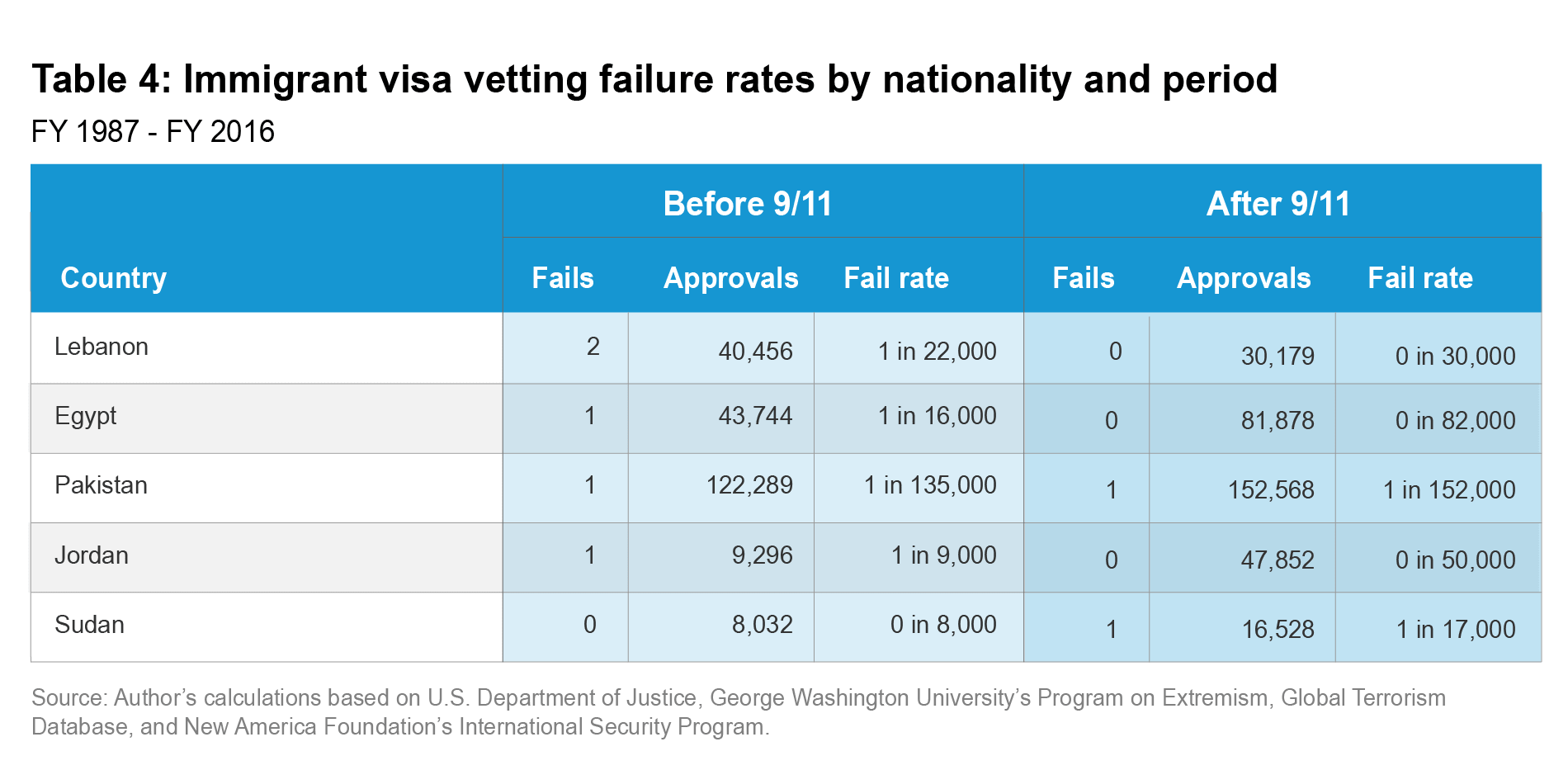
The president’s order specifically singles out immigrants (that is, foreigners entering from abroad to obtain legal permanent residency). It bars all immigrant visas to seven of the eight targeted nationalities, while allowing at least some temporary entries from most of those nationalities. For this reason, it is worth separately considering the vetting failure rates for immigrant visas by nationality. Immigrant visa vetting failures comprised only 11 percent of vetting failures from 1987 to 2016. As Table 4 shows, four nationalities had immigrant visa vetting failures in the 15 years leading up to 9/11, and two did after the attacks. Not shown in Table 4, nationals of the eight travel ban countries separately received 348,740 immigrant visas during this time, yet none of the immigrant vetting failures occurred among these nationals.
These declines are even more remarkable because the two most common terrorism offenses in the post-9/11 era—material support for terrorism and material support for a foreign terrorist organization—did not exist before 1994 and 1996, respectively.177 Moreover, DOJ rarely prosecuted individuals for offenses under these statutes until after 9/11, convicting just three individuals of such offenses from 1996 to 2001.178 They also rarely conducted FBI sting operations that targeted terrorism offenders, as they have routinely since 9/11.179
SECTION III: THE RISK FROM VETTING FAILURES
This analysis shows that vetting failures do happen, even if they are less frequent than they have been in the past. The president’s proclamation treats these failures as a very high risk to Americans, worthy of significantly more attention and government resources. But vetting failures represent only a very small portion of total terrorism offenders since 9/11; few of the terrorists have engaged in plots against Americans in the United States and these plots have resulted in an infinitesimally small share of homicides in the United States. The risk from these failures is not only small, but is growing smaller over time.
To consider post-9/11 vetting failures in context, Figure 4 includes offenders if their date of conviction or death occurred after 9/11, regardless of their date of entry. Of the 531 post-9/11 terrorism offenders, 94 percent did not enter the United States as a result of a vetting failure. As Figure 4 shows, more than 43 percent of terrorism offenders were born in the United States, 20 percent were extradited or intentionally lured into the country by a U.S. law enforcement sting, 14 percent entered when they were 15 years old or younger, and 15 percent entered as adults but radicalized after entry. Two terrorists (0.4 percent) entered illegally.180 Only 6 percent entered as a result of vetting failures, and two-thirds of those were prior to 9/11.
Setting aside individuals extradited or lured into the country by an FBI sting, only 35 offenders who were convicted or killed after 9/11 actually entered the United States after the September 11 attacks. Only 27 entered as adults (5 percent of all terrorism offenders) and only 13 of those were vetting failures. Thus, post-9/11 vetting failures account for just 2.45 percent of the 531 terrorism offenders convicted or killed after 9/11 (Table 5).
Terrorist Attacks as a Result of Vetting Failures
Even few vetting failures could carry serious risks for Americans. It is possible that despite the small numbers, the 13 post-9/11 failures created a risk equal to the 52 pre-9/11 failures. For this reason, it is important to analyze vetting failures based on whether the individuals who evaded vetting went on to plan to kill U.S. residents and whether those plans succeeded.
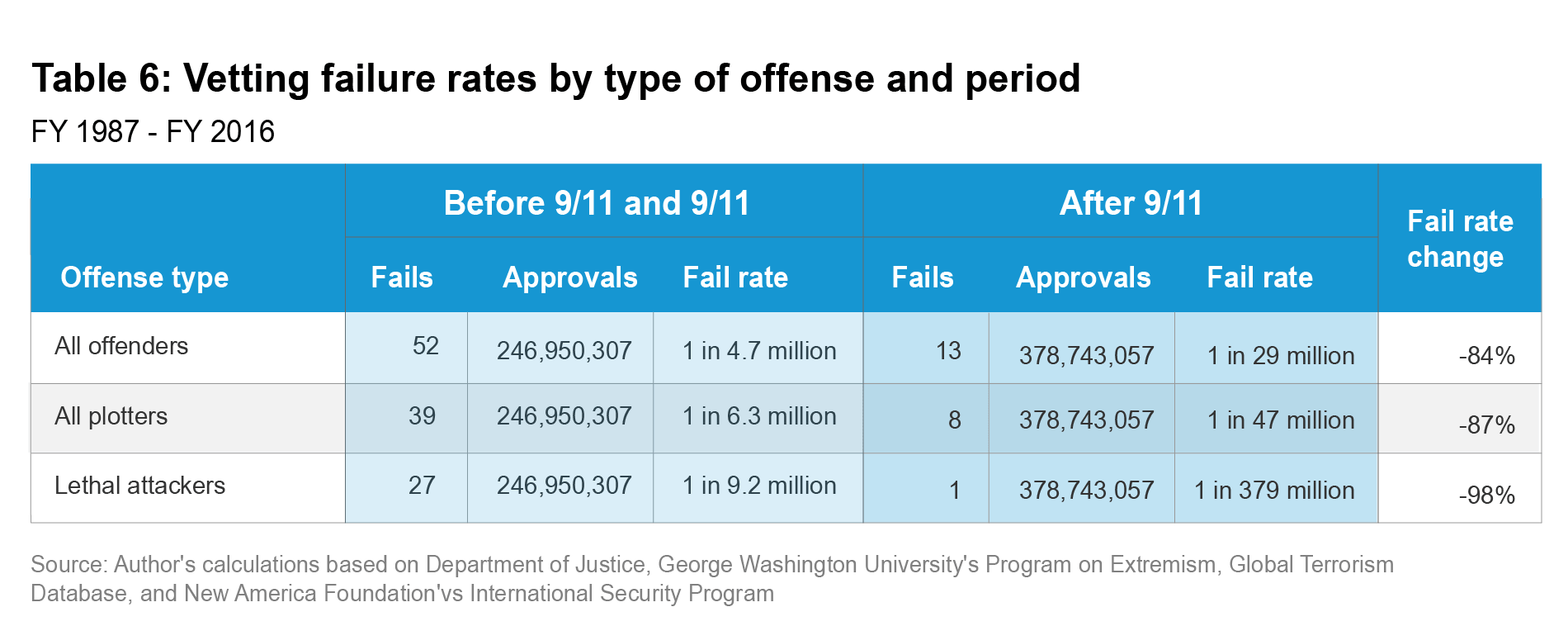
Such serious failures have also become even rarer than failures in general. Table 6 provides vetting failure rates based on the type of offense that the offender committed both before and after 9/11. It shows three offense types: "All Offenders" refers to vetting failures that resulted in any terrorism offense included in this analysis. "All Plotters" refers to a subset of all offenders: any vetting failures that allowed offenders to plot a terrorist attack in the United States regardless of whether they were able to carry it out. "Lethal Attackers" refers to a subset of all U.S. plotters: any plot that killed at least one resident in the United States who is not the attacker.
As Table 6 shows, vetting failure rates declined substantially for all three types of offenders. Vetting failures generally declined 84 percent after 9/11, but failures that permitted the entry of terrorists who plotted attacks targeting people in the United States declined 87 percent. Not only were fewer such terrorists admitted after 9/11, each individual was less dangerous than each one admitted before 9/11. Failures resulting in at least one death declined even further—98 percent from 1 in 9.2 million before 9/11 to 1 in 379 million after the attacks.
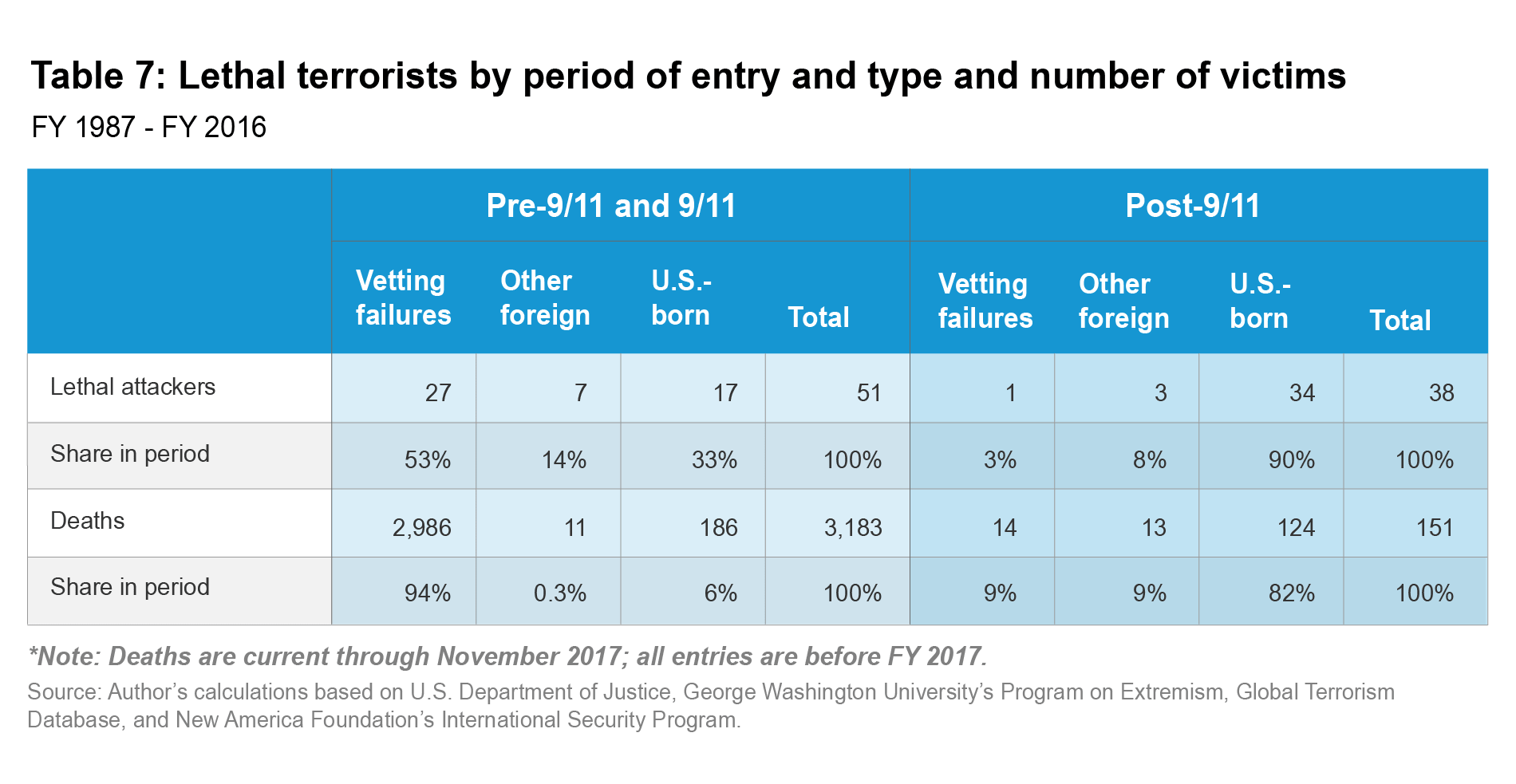
Even excluding the 9/11 hijackers, however, the rate of deadly vetting failures would still have declined over the 15-year period. Since 9/11, the U.S. government has granted entry to a population greater than that of the entire country for each deadly attacker it admitted. The difference in threat level becomes even more dramatic after factoring in the number of deaths that these attackers caused. Table 7 categorizes deaths based on the dates when their attackers entered the United States, not the dates of the attacks themselves, which is the date of interest because their entry created the risk for deaths later. After 9/11, vetting failures caused 9 percent of all terrorism deaths, killing 14 victims. Previously, vetting failures had accounted for a majority of lethal attackers and 94 percent of all terrorism deaths, killing 2,986 victims. This reduction accounts for almost all of the reduction in terrorism deaths since 9/11. From 1987 to 2001, the risk of death from vetting failures was 1 in 1.5 million per year. This means that terrorists killed 1 person in 1.5 million in the United States each year. Since 9/11, that risk has been reduced 99.5 percent—to 1 in 328 million annually. For comparison, the risk of death from a regular homicide during this period was 1 in 20,000 per year.181
The 2002 to 2016 vetting failure rate results could increase in the next couple of years because it is possible that some individuals who entered during those years will commit terrorist attacks after that period, just as some individuals who entered from 1987 to 2001 did after that period. However, from 2002 to 2016, one vetting failure was arrested about every 15 months, and the average time between entry and offense was about two and a half years. Therefore, based on current trends, two additional vetting failures are likely to reveal themselves during that period who had not yet carried out their offense as of October 2017. Given that there were 39 more vetting failures prior to 9/11, this possibility does not significantly affect the overall trends in this analysis.
SECTION IV: TERRORIST SCREENING AND INFILTRATION
Visa vetting failures have become rarer since 9/11. Possible explanations for this are that fewer terrorists attempted to enter during this time or that vetting procedures screen out more terrorists, or both. The former explanation is implausible. By nearly every possible measure, the number of foreign terrorists has grown dramatically. From 2000 to 2015, the number of foreign terrorist organizations doubled and their membership tripled.182 The number of foreign terrorism attacks and the number of deaths from terrorism outside the United States from 2001 to 2015 each doubled their totals from 1988 to 2000.183
Nor has immigration policy itself shifted away from areas that had visa vetting failures before 9/11. In fact, the number of visas or entries without visas for nationals of the 17 countries that had at least one vetting failure prior to 9/11 increased by 47 million. Indeed, only three such countries saw total flows decrease (see Table 3 above). Saudi Arabia had, by far, the most failures before 9/11 and it saw a 38 percent increase in visa issuances and refugee admissions since 9/11. Broader immigration policy simply cannot explain the drop in vetting failures.
Tougher immigration vetting likely played at least some role in preventing terrorist entries. As explained in Section I, the vetting improvements were specifically targeted at preventing a 9/11 style attack by a foreign terrorist group. The improvements appear to have specifically reduced failures for these types of terrorists.
Table 8 categorizes the 50 vetting failures for which we have some evidence regarding their pre-entry activities, statements, or beliefs. "Terrorist organization connections" refer to individuals for whom we have evidence that they contacted terrorist groups overseas before they entered the United States. "Other extremist associations" refer to those who had contact with other extremist individuals, and "personal statements" refer to individuals who claimed to have radicalized prior to entry or made private comments, but did not associate with other extremists prior to entry. The number of failures involving people with connections to foreign terrorist organizations has declined dramatically, while failures involving the other last categories has hardly changed.
This provides further evidence that the changes to the vetting system has driven some of the improvements in the drop in vetting failures. It makes sense that any enhancements in intelligence gathering would primarily affect those connected to known terrorist groups. Additionally, the government has actually denied visas to far more people based on concerns about terrorism. Congress first introduced a specific terrorism bar to entry in 1992; before that, terrorists were barred under general security grounds. From 1992 to 2001, State Department consular officers denied visas to 488 applicants on terrorism grounds—49 per year (Figure 5). After 9/11 they denied visas to 3,596 applicants on the same grounds—240 per year.184
The Department of Homeland Security screens VWP entrants, refugees, and asylees, but fails to report the number of denials as a result of terrorism concerns. Setting those categories aside, there were 32 State Department vetting failures from 1992 to 2001, and 8 failures from 2002 to 2016. Thus, terrorism screening excluded 15 applicants on terrorism grounds for each person it permitted to enter before 9/11, and excluded 450 for each person that it permitted to enter after 9/11. Had the screening continued at its pre-9/11 effectiveness, 29 times as many terrorists would have entered the United States after 9/11 as actually did.
While the government has not made precise statistics on refugee denials publicly available, it has stated that the security screening process has revealed that "hundreds of individuals from different countries, including hundreds of individuals from Syria, have had their admissions to the United States denied because of information that was found in these [national security] databases."185 Refugees present unique vetting challenges. Because they are displaced from their homes and countries, they have difficulty obtaining original identification and documentation. Instability in their home countries can also obstruct access to their government’s criminal records, and official persecution can also make such records unreliable in any case.
However, many refugee applicants will have previously had contact with the U.S. government directly through visa screening or employment or indirectly through family members in the United States, and biological relationships are documented through DNA testing.186 Several factors also mitigate the difficulty of obtaining records. First, unlike other immigrants, refugees generally cannot select their destination country in advance. The United Nations High Commissioner for Refugees (UNHCR) generally begins the process by referring less than 1 percent of all refugees to the United States (the others remain in UNHCR camps or elsewhere).187 By itself, this makes it statistically unlikely that a terrorist operation working through the refugee program would succeed.
Second, resettlement decisions are based on humanitarian concerns—situations in the country to which the refugee has fled that give rise to a reason for resettlement, such as unique medical needs or persistent persecution even in the country to which they have fled.188 These criteria further weed out would-be infiltrators without legitimate claims. Third, the U.S. resettlement refugee security screening process generally takes more than two years, with no guarantee of resettlement, creating a natural incentive for terrorists to seek other routes to attack the West.189 These factors could explain the few refugee screening errors before and after 9/11.
Policy Responses to the Visa Vetting Failures
U.S. policymakers have not ignored the post-9/11 vetting failures. In response to the vetting failure cases where the U.S. government found evidence of radicalization prior to entry, it further tightened its procedures. While technically a post-9/11 failure, the first vetting error occurred just three months after the September attack when Richard Reid, a British national who boarded a U.S.-bound flight under the VWP, attempted to detonate a bomb in his shoe during the flight.190 As previously mentioned, VWP travelers had little vetting prior to entry in 2001.
Reid also used multiple passports to cover his travel to terrorist training camps in Afghanistan and Pakistan.191 Today, all VWP passports must create electronic travel records, which would have alerted authorities to his movements.192 All airlines must now supply passenger-manifest information to DHS prior to flying, which allows DHS to check the new watchlists.193 As an operative in a larger network, Reid would have had a much greater chance of being watchlisted after 9/11 than before because the U.S. intelligence agencies shifted their attention toward terrorist travel and because VWP countries now must share intelligence with the United States on terrorists within their borders. VWP travelers now cannot board a plane without first receiving prior approval to travel under the Electronic System for Travel Authorization, which checks biographic information against law enforcement databases.
Umar Farouk Abdulmutallab’s Christmas Day attempt to detonate a bomb hidden in his underwear on a U.S.-bound flight in 2009 triggered the most comprehensive scrutiny of the vetting process since 9/11. His case is complex. Consular officers denied Abdulmutallab a tourist visa twice in 2004—first for applying too far from his place of residence, and then later for failing to disclose the denial when he reapplied.194 A supervisor reversed the second denial, a decision that initially had no negative repercussions for security. In 2008, when Abdulmutallab applied again for a tourist visa, however, he again incorrectly claimed to have never received a visa denial, yet the department’s system failed to notify the adjudicating officer to the earlier denials, which it considered "resolved" because of the supervisor’s override.195 Today, the vetting system provides consular officers the full case history of an applicant, including initial determinations.196
In 2008, the U.S. embassy in London granted Abdulmutallab a two-year, multiple-entry tourist visa.197 He flew to Houston to attend an Islamic seminar and left without incident.198 In October 2009, he traveled to Yemen to meet with Anwar al-Awlaki, a major al Qaeda leader, who encouraged him to carry out a U.S. attack.199 After Abdulmutallab’s father told U.S. embassy officials in Nigeria that he suspected his son may have radicalized, State notified the Terrorist Screening Center, and after some initial confusion over his name, a consular official classified Abdulmutallab as a "possible terrorist," the broadest classification in its CLASS watchlist and a designation that, at the time, would not have prevented him from boarding a plane.200 After this incident, however, DHS updated its Secure Flight airline manifest screening to create an expanded watchlist that would have included Abdulmutallab.201
In December 2009, State sought to revoke the visa, but a U.S. intelligence agency told it not to because it did not believe that Abdulmutallab was an immediate threat and did not want to tip him off to its surveillance, believing that he would help them unravel a larger conspiracy.202 In that way, the government directly attempted to allow him to enter the United States for the purpose of its investigation, which means this case is debatably not a vetting failure since procedures identified him before he traveled. State officials have admitted, however, that they possessed the independent authority to revoke his visa and updated the agency’s visa revocation policy in response to the attack.203 The new policy automatically revokes any visa to a person classified as a "possible terrorist."204 State also greatly expanded its law enforcement investigator positions to investigate similar cases of reported radicalization of current visa holders.205
DHS responded to the attack by increasing the number of Visa Security Units at visa posts, a policy that Senate Judiciary Committee Chairman Charles Grassley (R-IA) has said would also have prevented it.206 It expanded the use of full-body scanners to detect hidden explosives and swabbing people’s hands to detect explosive residue.207 The National Counterterrorism Center created specific teams designed to follow-up on tips, such as the one submitted by Abdulmutullab’s father.208 Perhaps most importantly, the United States began to share its visa application information with the United Kingdom, Canada, Australia, and New Zealand.209 Because Abdulmutallab attempted to obtain a British visa by fraud in May 2009, this measure could have also triggered a revocation of his visa.210
After the 2009 admission of Iraqi insurgents Waad Ramadan Alwan and Mohanad Shareef Hammadi as refugees, the FBI found Alwan’s fingerprints on a detonator for an improvised explosive device (IED) used to kill Americans in Iraq.211 This discovery enabled it to carry out a sting operation and arrest him and his friend for attempting to supply weapons to Iraqi insurgents in 2011.212 In response, the FBI created a new database of fingerprints drawn from its IED repository from Iraq and Afghanistan, a move that would have prevented Alwan’s admission.213
After Abdinasir Mohamud Ibrahim’s 2007 entry as a Somali refugee, the FBI discovered that he had lied on this refugee application about his clan affiliation; he was actually part of the Somali clan responsible for persecution of other clans, and was related to and friends with members of Al-Shabaab, the Somali terrorist group.214 While in the United States from 2007 to 2014, Ibrahim sent $100 to his friend, who was an Al-Shabaab member. He also lied about his age and other biographical details. Such fraud can be difficult to detect, but since 2007 the State Department, Department of Homeland Security, and United Nations High Commissioner for Refugees have each instituted numerous new measures to combat refugee fraud.215 In particular, the State Department has started to implement multiple prescreening interviews for refugees because "conducting more than one interview serves as a fraud deterrent because it allows the staff to check for consistency across interviews and identify false information."216
The Difficulty with Further Vetting Improvements
Given these changes, the government has very little opportunity to improve visa vetting in a meaningful way. The other eight vetting failure cases highlight the difficulty of going further. Jubair Ahmad, for example, did briefly train when he was 16 years old with Lashkar-e-Taiba (LeT), a foreign terrorist organization in Pakistan.217 The terrorists refused to train him until he was older. The problem is that Ahmad never applied for a visa for himself and appears to have never wanted to leave Pakistan. Instead, he received legal permanent residency as a derivative of his parents, who had applied for immigrant visas when he was 3 years old. After waiting 16 years, they received their approvals in 2006, and he also received a visa as a derivative applicant as a child under the age of 21. Rather than planning an attack upon his arrival, however, Ahmad repeatedly sought to return to Pakistan to join LeT. The FBI ultimately arrested him for posting a YouTube propaganda video for LeT.
San Bernardino shooter Tashfeen Malik’s husband sponsored her for a green card, and the administration determined that Malik met all the requirements to receive a visa—she was, in fact, a fiancée of a U.S. citizen—and "background checks did not reveal any derogatory information."218 At this point, she had not engaged in any illegal activity. Malik sent Facebook messages to a group of Pakistani friends expressing support for ISIS.219 While in Saudi Arabia, she also exchanged messages with Syed Rizwan Farook, her future husband and fellow attacker, about their mutual support for terrorism.220 After the San Bernardino attacks, the State Department began a pilot program of mandatory social-media screening at 17 foreign visa posts.221 (It expanded that effort in 2017.) But according to law enforcement officials, social-media screening would not have identified these messages because she had strict privacy settings and she used a pseudonym online to hide her identity.222
Several other vetting failures had even less information to go on. Quazi Mohammad Rezwanul Ahsan Nafis and Mahmoud Amin Mohamed Elhassan had researched extremist teachers Sami Osmakac and Anwar al-Awlaki prior to immigrating, but neither revealed their intentions publicly until after their arrival.223 Similarly, Khalid Ali-M Aldawsari blogged about his reasons for coming to the United States, but only after he entered—and then only under a pseudonym.224 Fazliddin Kurbanov claimed to have radicalized in response to the rape of a Muslim girl by U.S. soldiers in 2009.225 This statement is the only publicly known indication of pre-entry radicalization. For Hosam Maher Husein Smadi, no public information exists showing pre-entry radicalization. He entered as a 16-year-old and is classified as a vetting failure because he purportedly "indicated" to undercover agents that he had come to commit acts of terrorism, but there are several reasons to believe that this was untrue, and that he was only attempting to impress them.226
Of those cases lacking a documented connection to terrorist organizations overseas, only Ahmed Abdellatif Sherif Mohamed, who was born in Kuwait but possessed Egyptian citizenship, entered in January 2007 on a student visa and appears to have had a documented pre-entry terrorist history. Egyptian authorities detained him for four months on "terrorism-related charges" in 2003.227 He admitted on his visa application that he had been arrested, but he was issued a visa anyway.228 Immediately after his arrival in the United States he started to plan a terrorist attack, began to build a bomb, and attempted to purchase a rifle. He claimed to have previously trained with weapons overseas, but it is unknown if he had any foreign terrorist group affiliations.229
The Costs of Restrictions
The reality is that no vetting regime will ever catch every bad actor. The goal should be to identify the most dangerous, and the post-9/11 vetting system has proven especially capable of doing so. Because 9/11-style attacks are complex conspiracies, identifying even a single member as a conspirator in the plot would unravel it, making 100 percent accuracy unnecessary. The government has already responded to 9/11 and the visa vetting failures over the last 15 years in targeted ways, addressing the specific shortcoming that those failures revealed. Blindly enacting new requirements without any evidence that these standards are capable of protecting the country will only create unnecessary costs. The United States benefits greatly from immigrants and other foreign travelers, and further restrictions will simply harm Americans without any benefit.
The potential losses are substantial. Immigration produces an economic boon to U.S. natives of between $35 billion and $230 billion annually, and tourism adds another almost $200 billion.230 These figures exclude benefits to the immigrants themselves. According to the National Academy of Science’s 2016 report on the fiscal effects of immigration, immigrants, on average, pay between $92,000 and $173,000 more in taxes than they receive in benefits in net present value over their lifetime.231 The fiscal and economic gains pay, in part, for infrastructure, health care, and policing that improve—and even save—lives elsewhere.
Shutting off or greatly restricting immigration in response to terrorism simply cannot be justified. Using the highest estimate of the cost of a terrorism death, the Cato Institute’s 2016 report on the risk of foreign-born terrorism generally concluded that a moratorium on all immigration and tourism would have been justified over the last 41 years only if terrorism had killed more than 200 times as many people as it did.232 This estimate included 9/11, but as this analysis has already documented, another 9/11 style attack has become far less likely.
Even modest restrictions will impose costs that fail to equal the benefits. That is partly because the possible benefits—a reduction of less than one death per year—are so miniscule, but also because, as research from other risk-reduction domains has shown, attempts to reduce risk below already negligible levels becomes exponentially more expensive since all the easiest fixes have already been completed.233 The risk of vetting failures is already approaching zero. Further investments will yield few benefits.
Conclusion
The United States already practices "extreme vetting." While people of all types—foreign-born or U.S.-born—will always pose certain risks to the country, the country has maxed out its capacity to improve immigration vetting. Fortunately, vetting failures are very rare and pose a small risk to the United States. The United States can continue to accept immigrants from around the world with the knowledge that vetting has improved tremendously since the catastrophic failure on 9/11. The government needs to remain on the lookout for potential threats, but the evidence indicates that its existing processes are already succeeding in weeding out terrorists. This conclusion suggests that if the government insists on additional security spending, it should prioritize domestic counterterrorism efforts over visa vetting.
This analysis also demonstrates that neither terrorism as a result of vetting failures nor terrorism as a result of failed assimilation presents significant threats to Americans. About 230,000 more Americans were murdered in nonterrorism homicides than were killed by terrorists of all kinds in the United States from 2002 to 2016.234 Of course, another 9/11 style terrorist attack should concern U.S. law enforcement, but the post-9/11 reforms to visa vetting, in conjunction with improved airline security, make such a complex conspiracy vastly more difficult to accomplish. For these reasons, terrorism should play only a minor role in debates over immigration going forward. The government should continue its pre-Trump administration policies to prevent such attacks and not erect new unnecessary barriers to legal immigration.
APPENDIX A
Terrorism-related offenses
Terrorism offenses
- 18 U.S.C. 32 (aircraft sabotage, 1 conviction)
- 18 U.S.C. 43 (animal enterprise terrorism, 2 convictions)
- 18 U.S.C. 175, 175b, 229, 831, 2332a: (Use of biological, nuclear, chemical or other weapons of mass destruction, 37 convictions)
- 18 U.S.C. 956 (conspiracy within the United States to murder, kidnap, or maim persons or to damage verified property overseas, 23 convictions)
- 18 U.S.C. 1203 (hostage taking, 5 convictions)
- 18 U.S.C. 1993 (terrorist attacks against mass transportation systems, 1 conviction)
- 18 U.S.C. 2332 (terrorist acts abroad against United States nationals, 2 convictions)
- 18 U.S.C. 2332b (terrorism transcending national boundaries, 3 convictions)
- 18 U.S.C. 2332f (bombings of places of public use, government facilities, public transportation systems and infrastructure facilities, 2 convictions)
- 18 U.S.C. 2332g (missile systems designed to destroy aircraft, 12 convictions)
- 18 U.S.C. 2339A (providing material support to terrorists, 113 convictions)
- 18 U.S.C. 2339B (providing material support to designated terrorist organizations, 136 convictions)
- 18 U.S.C. 2339C (prohibition against financing of terrorism, 2 convictions)
- 18 U.S.C. 2339D (receiving military-type training from an FTO, 4 convictions)
- 21 U.S.C. 1010A (narcoterrorism, 1 conviction)
- 49 U.S.C. 46502 (aircraft piracy, 3 convictions)
- 18 U.S.C. 1114, 1117 (attempted murder, murder of government employees, 26 convictions)*
- 18 U.S.C. 371-73 (conspiracy, 30 offenses)*
- 22 U.S.C. 2778 (arms export controls, 3 convictions)*
- Killed during terrorism offense, 31 cases*
*Not included by the U.S. Department of Justice as a Category I terrorism offense
Nonterrorism offenses
- 18 U.S.C. 1001, 1542, 1014, 1015(a) (false statements to investigators, 63 convictions)
- 18 U.S.C. 1028, 1543-46 (ID/visa/passport fraud, 64 convictions)
- 18 U.S.C. 1956 (money laundering, 50 convictions)
- 8 U.S.C. 1101-1778; 18 U.S.C. 1425, 1015 (immigration, 40 convictions)
- 18 U.S.C. 1029, 1331-34,513,157 15 U.S.C. 78j; and 31 U.S.C. 5324 (credit card, bank, bankruptcy, wire, securities fraud; structuring financial payments to avoid reporting, 29 convictions)
- 18 U.S.C. 922, 26 U.S.C. 5861 (firearms, 16 convictions)
- 18 U.S.C. 1962 (racketeering, 15 convictions)
- 18 U.S.C. 1519, 1505, 1512, 1503 (obstruction of investigations/witness tampering/juror threats, 12 convictions)
- 26 U.S.C. 7212 (taxes, 7 convictions)
- 18 U.S.C. 2320, 2314, 2315 (transportation or sale of stolen or counterfeit goods, 10 convictions)
- 21 U.S.C. 844, 952, 959, 963 (drugs, 6 convictions)
- 50 U.S.C. 1701-6 (violating sanctions, 6 convictions)**
- 18 U.S.C. 1621-23, 26 U.S.C. 7206, 28 U.S.C. 1746 (perjury, 6 convictions)
- 22 U.S.C. 612 (failure to register as foreign agent, 4 convictions)
- 18 U.S.C. 2342 (contraband cigarettes, 2 convictions)
- 42 U.S.C. 408 (Social Security fraud, 5 convictions)
- 31 U.S.C. 5332 (cash smuggling, 2 convictions)
- 18 U.S.C. 3147 (parole violation, 1 conviction)
- 18 U.S.C. 35, 844 (bomb hoax threats, 3 convictions)
- 18 U.S.C. 401 (contempt of court, 1 conviction)
- 18 U.S.C. 545 (smuggling, 1 conviction)
- 10 U.S.C. 92 (robbery, 1 conviction)
- 18 U.S.C. 371-73 (conspiracy, 56 offenses)
- 18 U.S.C. 2252 (child pornography, 1 conviction)
**Included by U.S. Department of Justice as a Category I terrorism offense
APPENDIX B
Terrorism offenders
Sources for names for all tables: U.S. Department of Homeland Security, U.S. Department of State, U.S. Department of Justice, George Washington University’s Program on Extremism, and New America Foundation’s International Security Program.
Key: U.S. Plot = planned attack in the United States; Status = visa or status at first entry; B = tourist; F = student; LPR = legal permanent resident; VWP = Visa Waiver Program; R = refugee; K = fiancé/fiancée; U = unknown; Info = type of information missed in vetting; NA = none available; TC = terrorist group connections; TA = terrorism associations; PS = personal statements.
* = Illegally entered or arrested at a border.
Infogram
Notes
1. Sec. 2(c) of Executive Order 13780, "Executive Order Protecting the Nation from Foreign Terrorist Entry into the United States," March 6, 2017, https://www.whitehouse.gov/the-press-office/2017/03/06/executive-order-protecting-nation-foreign-terrorist-entry-united-states.
2. 8 U.S.C. § 1361.
3. Bureau of Consular Affairs, "Forms," Department of State, October 13, 2017, https://travel.state.gov/content/visas/en/forms.html.
4. 8 U.S.C. § 1201–1202.
5. 8 U.S.C. § 1202.
6. 8 U.S.C. § 1202.
7. Leon Rodriguez, Testimony on "The Security of the U.S. Visa Programs" before the Senate Committee on Homeland Security and Governmental Affairs, March 15, 2016, https://www.uscis.gov/tools/resources-congress/testimonies-and-speeches/hearing-security-us-visa-programs-senate-committee-homeland-security-and-governmental-affairs-march-15-2016-uscis-director-leon-rodriguez.
8. U.S. Citizenship and Immigration Services, "Initial Review," Department of Homeland Security, https://egov.uscis.gov/cris/Dashboard/CaseStatus/BucketDescriptions.do.
9. Rodriguez, Testimony on "The Security of the U.S. Visa Programs."
10. U.S. Citizenship and Immigration Services, "Petition Process Overview," March 31, 2011, https://www.uscis.gov/working-united-states/information-employers-employees/petition-process-overview.
11. David Donahue, Testimony before the United States Senate Committee on Homeland Security and Governmental Affairs, March 15, 2016, https://www.hsgac.senate.gov/hearings/the-security-of-us-visa-programs.
12. Daniel Morgan and William Krouse, "Biometric Identifiers and Border Security: 9/11 Commission Recommendations and Related Issues," Congressional Research Service, February 7, 2005, https://fas.org/sgp/crs/homesec/RS21916.pdf; and Ruth Ellen Wasem, "Immigration: Visa Security Policies," Congressional Research Service, November 18, 2015, https://fas.org/sgp/crs/homesec/R43589.pdf.
13. Wasem, "Immigration: Visa Security Policies."
14. Donahue, Testimony.
15. Donahue, Testimony.
16. Donahue, Testimony.
17. Donahue, Testimony.
18. Ron Nixon, "U.S. to Further Scour Social Media Use of Visa and Asylum Seekers," New York Times, February 23, 2016, https://www.nytimes.com/2016/02/24/us/politics/homeland-security-social-media-refugees.html; and Doina Chiacu, "Homeland Security Chief Says Social Media Used in Immigration Vetting," Reuters, December 16, 2015, http://www.reuters.com/article/us-usa-security-vetting-idUSKBN0TZ2C1201….
19. Donahue, Testimony.
20. Donahue, Testimony.
21. "Infographic: The Screening Process for Refugee Entry into the United States," Obama White House, November 20, 2015, https://obamawhitehouse.archives.gov/blog/2015/11/20/infographic-screening-process-refugee-entry-united-states.
22. Devon Cone, "The Process for Interviewing, Vetting and Resettling Syrian Refugees in America Is Incredibly Long and Thorough," Foreign Policy, November 20, 2015, http://foreignpolicy.com/2015/11/30/the-process-for-interviewing-vetting-and-resettling-syrian-refugees-in-america-is-incredibly-long-and-thorough/.
23. Legal Information Institute, "8 U.S. Code § 1187—Visa Waiver Program for Certain Visitors," Cornell Law School, https://www.law.cornell.edu/uscode/text/8/1187.
24. U.S. Customs and Border Protection, "Electronic System for Travel Authorization," September 30, 2016, https://www.cbp.gov/travel/international-visitors/esta.
25. U.S. Department of Homeland Security, "Implementing 9/11 Commission Recommendations," 2011, https://www.dhs.gov/xlibrary/assets/implementing-9-11-commission-report-progress-2011.pdf.
26. U.S. Department of Homeland Security, "Privacy Impact Assessment for the TECS System: CBP Primary and Secondary Processing," December 22, 2010, https://www.dhs.gov/xlibrary/assets/privacy/privacy-pia-cbp-tecs.pdf.
27. Rodriguez, Testimony on "The Security of the U.S. Visa Program."
28. U.S. Department of Homeland Security, "Privacy Impact Assessment for the TECS System."
29. U.S. Citizenship and Immigration Services, "Conditions of Secondary Inspection," 1997, https://www.uscis.gov/ilink/docView/FR/HTML/FR/0-0-0-1/0-0-0-30133/0-0-0-35080/0-0-0-36316/0-0-0-36468.html.
30. Thomas R. Eldridge, Susan Ginsburg, Walter T. Hempel II, Janice L. Kephart, and Kelly Moore, "9/11 and Terrorist Travel: Staff Report of the National Commission on Terrorist Attacks upon the United States," August 21, 2004, http://govinfo.library.unt.edu/911/staff_statements/911_TerrTrav_Monograph.pdf.
31. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," preface.
32. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 82.
33. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 126.
34. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 120.
35. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 129.
36. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 119.
37. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 142.
38. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 119.
39. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 35.
40. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 138.
41. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 122.
42. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 139.
43. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 76.
44. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 76.
45. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 34.
46. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 82.
47. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 34.
48. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," pp. 117–118, 122.
49. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 133.
50. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 136.
51. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," pp. 136–137.
52. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 87.
53. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 135.
54. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 133.
55. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 139.
56. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 137.
57. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 137.
58. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 134.
59. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 135.
60. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 135.
61. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 69.
62. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 68.
63. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," pp. 89, 151.
64. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 28.
65. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 81.
66. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 79.
67. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 94.
68. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 68.
69. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. X.
70. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 81.
71. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 81.
72. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 80.
73. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 80.
74. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 74.
75. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 24.
76. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 29.
77. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 133.
78. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 5.
79. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 143.
80. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 143.
81. Mark Potter and Rich Phillips, "Six Months after Sept. 11, Hijackers’ Visa Approval Letters Received," CNN, March 13, 2002, http://www.cnn.com/2002/US/03/12/inv.flight.school.visas/.
82. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 86.
83. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 133.
84. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 88.
85. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 104. For 2000 and 2001, see U.S. Bureau of Consular Affairs, " Table XX: Immigrant and Nonimmigrant Visa Ineligibilities," U.S. Department of State, Report of the Visa Office, 2000, https://travel.state.gov/content/dam/visas/Statistics/FY2000%20table%20XX.pdf; and U.S. Bureau of Consular Affairs, " Table XX: Immigrant and Nonimmigrant Visa Ineligibilities," U.S. Department of State, Report of the Visa Office, 2001, https://travel.state.gov/content/dam/visas/Statistics/FY2001%20table%20….
86. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 142.
87. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 30.
88. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 30.
89. 8 U.S.C. §1734.
90. Maura Harty, Testimony before the National Commission on Terrorist Attacks upon the United States, U.S. Department of State, January 26, 2004, https://2001-2009.state.gov/r/pa/ei/othertstmy/32988.htm.
91. Government Accountability Office, "Strengthened Visa Process Would Benefit from Improvements in Staffing and Information Sharing," GAO-05-859, September 2005, http://www.gao.gov/assets/250/247740.pdf.
92. Janice Kephart, Testimony on "Visa Security: Preventing Terrorists from Abusing U.S. Immigration Policy" before the House Judiciary Subcommittee on Immigration Policy and Enforcement, May 11, 2001, https://judiciary.house.gov/_files/hearings/pdf/Kephart05112011.pdf.
93. Harty, Testimony.
94. Harty, Testimony.
95. Harty, Testimony.
96. For 2002 and 2005, see Government Accountability Office, "Strengthened Visa Process Would Benefit from Improvements in Staffing and Information Sharing." For 2011 and 2014, see Government Accountability Office, "State Has Reduced Applicant Interview Wait Times, but Sustainability of Gains Is Uncertain," GAO-15-773, September 2015, http://www.gao.gov/assets/680/672379.pdf.
97. Congressional Research Service, "The Terrorist Screening Database: Background Information," June 17, 2016, https://www.everycrsreport.com/files/20160617_R44529_e24dca37574ac5bd794a0ce5333cab2cada5a306.pdf.
98. National Counterterrorism Center and the Federal Bureau of Investigation, "Response to Senator Dianne Feinstein," June 17, 2016, https://www.feinstein.senate.gov/public/_cache/files/f/b/fb745343-1dbb-4802-a866-cfdfa300a5ad/BCD664419E5B375C638A0F250B37DCB2.nctc-tsc-numbers-to-congress-06172016-nctc-tsc-final.pdf.
99. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 78; and Congressional Research Service, "The Terrorist Screening Database: Background Information."
100. Jerome P. Bjelopera, Bart Elias, and Alison Siskin, "The Terrorist Screening Database and Preventing Terrorist Travel," Congressional Research Service, November 7, 2016, https://fas.org/sgp/crs/terror/R44678.pdf.
101. Bjelopera et al., "The Terrorist Screening Database and Preventing Terrorist Travel"; and Eldridge et al., "9/11 and Terrorist Travel: Staff Report."
102. Bjelopera et al., "The Terrorist Screening Database and Preventing Terrorist Travel."
103. Harsha Panduranga, Faiza Patel, and Michael W. Price, "Extreme Vetting and the Muslim Ban," Brennan Center for Justice, October 2, 2017, https://www.brennancenter.org/sites/default/files/publications/extreme_vetting_full_10.2_0.pdf.
104. U.S. Citizenship and Immigration Services, "Refugee Processing and Security Screening," December 3, 2015, https://www.uscis.gov/refugeescreening.
105. U.S. Department of Homeland Security, "Implementing 9/11 Commission Recommendations."
106. David Inserra and Riley Walters, "The Visa Waiver Program: Enhancing Security, Promoting Prosperity," Heritage Foundation, September 16, 2014, http://www.heritage.org/immigration/report/the-visa-waiver-program-enhancing-security-promoting-prosperity#_ftn6.
107. U.S. Department of State, "Agreement between the United States of America and the European Union on the Use and Transfer of Passenger Name Records to the United States Department of Homeland Security," December 14, 2011, https://www.state.gov/documents/organization/203033.pdf.
108. Harty, Testimony.
109. U.S. Department of State, "FY 2002 Performance and Accountability Report," https://2009-2017.state.gov/s/d/rm/rls/perfrpt/2002/html/19015.htm; and Wasem, "Immigration: Visa Security Policies."
110. Ruth Ellen Wasem, "Visa Issuances: Policy, Issues, and Legislation," Congressional Research Service, October 13, 2004, http://trac.syr.edu/immigration/library/P9.pdf.
111. Government Accountability Office, "Border Security: State Could Enhance Visa Fraud Prevention by Strategically Using Resources and Training," GAO-12-888, September 2012, http://www.gao.gov/assets/650/647871.pdf.
112. Government Accountability Office, "Border Security: State Department Rollout of Biometric Visas on Schedule, but Guidance Is Lagging," GAO-04-1001, September 2004, http://www.gao.gov/assets/250/244011.pdf.
113. Government Accountability Office, "US-VISIT Program Faces Strategic, Operational, and Technological Challenges at Land Ports of Entry," GAO-07-248, December 2006, http://www.gao.gov/assets/260/254247.pdf.
114. Government Accountability Office, "Security of New Passports and Visas Enhanced, but More Needs to Be Done to Prevent Their Fraudulent Use," July 2007, http://www.gao.gov/assets/270/264809.pdf.
115. Charles E. Grassley, "Letter to Honorable Jeh Johnson," U.S. Senate Committee on the Judiciary, June 27, 2016, https://www.judiciary.senate.gov/imo/media/doc/2016-06-27%20CEG%20to%20DHS%20(VSP%20Status).pdf; and Gary L. Cote, Deputy Assistant Director for International Affairs, Immigration and Customs Enforcement, Testimony on "The Visa Security Program," before the House Committee on the Judiciary, Subcommittee on Immigration Policy and Enforcement," May 11, 2011, https://www.dhs.gov/news/2011/05/11/testimony-deputy-assistant-director….
116. U.S. Department of Homeland Security, "Implementing 9/11 Commission Recommendations."
117. U.S. Department of Homeland Security, "Implementing 9/11 Commission Recommendations."
118. U.S. Department of Homeland Security, "Implementing 9/11 Commission Recommendations."
119. Alison Siskin, "Visa Waiver Program," Congressional Research Service, December 11, 2015, https://fas.org/sgp/crs/homesec/RL32221.pdf.
120. U.S. Department of State, "Visa Waiver Program," https://travel.state.gov/content/travel/en/us-visas/tourism-visit/visa-waiver-program.html.
121. U.S. Department of State Office of Inspector General, "Review of Nonimmigrant Visa Issuance Policy and Procedures," December 2002, https://oig.state.gov/system/files/16215.pdf.
122. Executive Order 13769, "Executive Order Protecting the Nation from Foreign Terrorist Entry into the United States," January 27, 2017, https://www.whitehouse.gov/the-press-office/2017/01/27/executive-order-protecting-nation-foreign-terrorist-entry-united-states.
123. Executive Order 13780, "Executive Order Protecting the Nation from Foreign Terrorist Entry into the United States," March 6, 2017.
124. Sec. 5 and Sec. 3(c), respectively, of Executive Order 13769, "Executive Order Protecting the Nation from Foreign Terrorist Entry into the United States"; and Sec. 6 and Sec. 2(c), respectively, of Executive Order 13780, "Executive Order Protecting the Nation from Foreign Terrorist Entry into the United States."
125. Sec. 1(h) of Executive Order 13780.
126. Sec. 2(a) and (b) of Executive Order 13780, "Executive Order Protecting the Nation from Foreign Terrorist Entry into the United States."
127. Department of Homeland Security Office of Intelligence and Analysis, "Intelligence Assessment: Most Foreign-Born, US-based Violent Extremists Radicalized after Entering Homeland; Opportunities for Tailored CVE Programs Exist," March 2017, https://upload.wikimedia.org/wikipedia/commons/b/ba/Most_Foreign-born%2C_US-based_Violent_Extremists_Radicalized_after_Entering_Homeland.pdf.
128. Department of Homeland Security Office of Intelligence and Analysis, "Intelligence Assessment," p. 1.
129. 82 Federal Register 45161, Enhancing Vetting Capabilities and Processes for Detecting Attempted Entry into the United States by Terrorists or Other Public-Safety Threats," https://www.gpo.gov/fdsys/granule/FR-2017-09-27/2017-20899.
130. Department of Homeland Security and Department of Justice, Executive Order 13780, "Executive Order Protecting the Nation from Foreign Terrorist Entry into the United States, Initial Section 11 Report," January 2018, https://www.justice.gov/opa/press-release/file/1026436/download.
131. Department of Homeland Security and Department of Justice, Executive Order 13780, "Executive Order Protecting the Nation from Foreign Terrorist Entry into the United States, Initial Section 11 Report," p. 7.
132. In one case, it also relied on a statement provided to the author by an attorney for the offender.
133. Department of Justice National Security Division, "Chart of Public/Unsealed International Terrorism and Terrorism-Related Convictions from 9/11/01 to 12/31/15," August 26, 2016, https://object.cato.org/sites/cato.org/files/wp-content/uploads/dojterrorismrelatedconvictions2015.pdf.
134. New America Foundation, "Terrorism in America after 9/11," https://www.newamerica.org/in-depth/terrorism-in-america/; George Washington University Program on Extremism, "The Cases," https://extremism.gwu.edu/cases; and Sarah Gilkes, "Not Just the Caliphate," George Washington University, December 2016, https://extremism.gwu.edu/sites/extremism.gwu.edu/files/downloads/Not%2….
135. Eldridge et al., "9/11 and Terrorist Travel: Staff Report"; and Alex Nowrasteh, "Terrorism and Immigration: A Risk Analysis," Cato Institute Policy Analysis no. 798, September 13, 2016, https://www.cato.org/publications/policy-analysis/terrorism-immigration-risk-analysis.
136. University of Maryland, "Global Terrorism Database," http://www.start.umd.edu/gtd/. The number from 1993 is unavailable, so I used the number from RAND National Security Division, "RAND Database of Worldwide Terrorism Incidents," https://www.rand.org/nsrd/projects/terrorism-incidents.html.
137. The defendant is Adriana Gladys Mora. In any case, the offender grew up in the United States from a young age and would not be a vetting failure. United States of America v. Adriana Gladys Mora, U.S. District Court Southern District of Texas, "Character Letters," October 31, 2005, https://object.cato.org/sites/cato.org/files/wp-content/uploads/gladys.pdf.
138. In a few instances, reports indicated only that the person was a "child," presumably 15 years old or younger.
139. Department of Justice National Security Division, "Chart of Public/Unsealed International Terrorism and Terrorism-Related Convictions from 9/11/01 to 12/31/15."
140. It also excludes six Category I offenders who were convicted of violating Iraqi sanctions during the 1990s for donating to Iraqi relief organizations because their actions had no relationship to terrorism or a terrorist organization.
141. University of Maryland, Global Terrorism Database, "Criterion," https://www.start.umd.edu/gtd/more/Criterion.aspx#one.
142. "Since 2001, we have revoked 57,000 visas for a variety of reasons, including over 2,800 for suspected links to terrorism." Janice L. Jacobs, Testimony on "The Lessons and Implications of the Christmas Day Attack: Securing the Visa Process," before the U.S. Senate Committee on Homeland Security and Governmental Affairs, April 21, 2010, https://object.cato.org/sites/cato.org/files/wp-content/uploads/testimonyjacobs20100421.pdf. "Since 2001, the Department has revoked over 122,000 visas for a variety of reasons, including nearly 9,500 for suspected links to terrorism." See "Terrorist Travel: Vetting for National Security Concerns," Committee on Oversight and Government Reform, December 17, 2015, https://oversight.house.gov/wp-content/uploads/2015/12/2015-12-17-FC-Te….
143. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 2.
144. The United States of America v. Ali Saleh Kahlah Al-Marri, "Complaint," Southern District of New York, Case No. 03-10044, December 2002, http://news.findlaw.com/hdocs/docs/almarri/usalmarri1202cmp.html.
145. The United States of America v. Ali Saleh Kahlah Al-Marri.
146. The United States of America v. Ali Saleh Kahlah Al-Marri, p.8.
147. Michael Elliott, "The Shoe Bomber’s World," Time, February 16, 2002, http://content.time.com/time/world/article/0,8599,203478-3,00.html.
148. U.S. Department of State, "Required Documents for a Visa Application," http://photos.state.gov/libraries/48675/Cons%20PDFs/130517--Checklist%20Required%20Documents%20Renewing%20a%20B1%20B2%20visa%20ENGLISH.pdf.
149. Mohammad Hassan Khalid is the youngest charged person in the data assembled in this analysis.
150. Eldridge et al., "9/11 and Terrorist Travel: Staff Report," p. 154.
151. Mark S. Hamm and R. F. J. Spaaij, The Age of Lone Wolf Terrorism (New York: Columbia University Press, 2017), pp. 243–49.
152. "Sentencing Delayed for Terror Supporter in Florida," Associated Press, November 20, 2014, http://www.cnsnews.com/news/article/sentencing-delayed-terror-supporter-florida.
153. Majority Staff of the Committee on Homeland Security, "The Road to Boston: Counterterrorism Challenges and Lessons from the Marathon Bombings," House Homeland Security Committee, March 2014, https://homeland.house.gov/files/documents/Boston-Bombings-Report.pdf.
154. Josh White and Allison Klein, "Pentagon Shooting Suspect Not Known to Law Enforcement," Washington Post, June 23, 2011, https://www.washingtonpost.com/local/pentagon-shooting-suspect-not-known-to-law-enforcement/2011/06/23/AGniB8hH_story.html.
155. "Terror Suspect’s Wife: ‘He Loves America,’" CBS News, January 8, 2016, https://www.cbsnews.com/news/terror-suspect-omar-al-hardan-wife-he-loves-america/; and "Iraqi Refugee Living in Houston Pleads Guilty to Trying to Help ISIS," CBS News, October 17, 2016, http://www.cbsnews.com/news/iraqi-refugee-living-in-houston-pleads-guil….
156. Thomson Reuters, "Ulugbek Kodirov Jailed 16 Years for Plot to Assassinate President Obama," PRI, July 13, 2012, https://www.pri.org/stories/2012-07-13/ulugbek-kodirov-jailed-16-years-plot-assassinate-president-obama.
157. Jeff Seldin, "Fears Growing Islamic State Successfully Weaponizing Refugees," Voice of America, December 24, 2016, https://www.voanews.com/a/islamic-state-refugees-europol-report/3649183.html; and Matt Zapotosky, Susan Svrluga, Alejandra Matos, and Ellen Nakashima, "FBI: Ohio State Attacker Might Have Been Inspired by Islamic State," Washington Post, November 30, 2016, https://www.washingtonpost.com/news/grade-point/wp/2016/11/30/fbi-ohio-….
158. United States of America v. Akhror Saidakhmetov, "Defendant Akhror Saidakhmetov’s Memorandum in Aid of Sentencing," Case No. 15-00095, October 11, 2017, https://object.cato.org/sites/cato.org/files/wp-content/uploads/saidahkmetov.pdf.
159. Jeff Montgomery, Esteban Parra, and Cris Barrish, "FBI: Mall Kiosk Owner Financed Islamic State Plot," USA Today, February 27, 2017, https://www.usatoday.com/story/news/nation/2015/02/27/fbi-mall-kiosk-owner-financed-isis-plot/24107959/.
160. Joseph De Avila, Rebecca Davis O’Brien, and Pervaiz Shallwani, "Brooklyn Men’s Alleged Plot to Join ISIS Foiled by Online Posts," Wall Street Journal, February 27, 2015, https://www.wsj.com/articles/brooklyn-mens-alleged-plot-to-join-isis-foiled-by-online-posts-1424989004.
161. "In recent weeks he set in motion a plan—to join his friend and go fight with the Islamic State.... In recent weeks, he increasingly demanded seclusion. He was a very different man from the one who went to Mr. Khan in June begging for a job." As quoted in Marc Santora and Nate Schweber, "In Brooklyn, Eager to Join ISIS, If Only His Mother Would Return His Passport," New York Times, February 26, 2015, https://www.nytimes.com/2015/02/27/nyregion/isis-plot-brooklyn-men.html. Also see "Educating himself for the first time about Islam, Juraboev met some wrong people and reached some wrong conclusions about Islam and ISIL.… Seeking a community, Abdurasul joined a mosque and began studying the Koran. As he studied, he became more and more religious, a process that intensified when Abdurasul fell ill in 2012." See United States of America v. Abdurasul Hasanovich Juraboev, "Abdurasul Hasanovich Juraboev’s Sentencing Memorandum," Case No. 15-00095, October 18, 2017.
162. Mark Berman and Matt Zapotosky, "Investigators Probe New York Attack Suspect’s Communications While Trump Calls for Death Penalty," Washington Post, November 2, 2017, https://www.washingtonpost.com/news/post-nation/wp/2017/11/02/investigators-probe-new-york-attack-suspects-communications-while-trump-calls-for-death-penalty/.
163. United States v. Agron Hasbajrami, "Government Sentencing Memorandum," Case No. 11-623, August 11, 2015, https://www.investigativeproject.org/documents/case_docs/2814.pdf.
164. United States v. Agron Hasbajrami, "Sentencing Memorandum," Case No. 11-623, July 15, 2015, https://object.cato.org/sites/cato.org/files/wp-content/uploads/hasbajramisentencingmemo.pdf.
165. Scott Schwebke, "Former Anaheim Cab Driver, Convicted on Terrorism Charges, Deported to Somalia," Orange County Register, November 2, 2016.
166. United States of America v. Ahmed Nasir Taalil Mohamud, "Judgment & Sentence," United States District Court Southern District of California, January 31, 2014, https://object.cato.org/sites/cato.org/files/wp-content/uploads/ahmedtaalilmohamudsentencinghearing.pdf.
167. On the subject of "threatened," see United States of America v. Muna Osman Jama et al., "Government’s Sentencing Memorandum," Case No. 14-00230, February 14, 2017, https://object.cato.org/sites/cato.org/files/wp-content/uploads/jamasentencingmemo.pdf. On the subject of "expelled," see United States of America v. Amina Mohamud Esse, "Defendant’s Position as to Sentencing Factors and Sentencing Memorandum," Case No. 14-00369, February 13, 2017, https://object.cato.org/sites/cato.org/files/wp-content/uploads/esseami….
168. Scott Dolan and Megan Doyle, "Documents: Freeport Man Died Fighting for Islamic State in Lebanon," Press Herald, August 16, 2016, http://www.pressherald.com/2016/08/16/documents-freeport-man-died-fighting-for-islamic-state/.
169. United States v. Zubair Ahmed and Khaleel Ahmed, "Government’s Sentencing Memorandum," U.S. District Court for the Northern District of Ohio Western Division, July 1, 2010, https://object.cato.org/sites/cato.org/files/wp-content/uploads/khaleelahmed.pdf.
170. Sources related to Siraj: 151 Cong. Rec. 2026 (2005) (Statement of John Conyers), https://www.congress.gov/crec/2005/02/10/CREC-2005-02-10-pt1-PgH536-3.pdf; and John Mueller, ed., Terrorism Since 9/11: The American Cases (Columbus: Ohio State University, March 2016). Sources related to Abraham: Trevor Aaronson, "The Released," Intercept, April 20, 2017, https://theintercept.com/2017/04/20/more-than-400-people-convicted-of-t….
171. United States of America v. Patrick Abraham, "Sentencing Hearing," Case No. 06-20373, November 19, 2009, https://object.cato.org/sites/cato.org/files/wp-content/uploads/abrahamsentencinghearing.pdf.
172. Bob Campbell, "1997 Republic of Texas Standoff Intense, Damaging to Participants," Midland Reporter-Telegram, April 21, 2007, http://www.mrt.com/news/article/1997-Republic-of-Texas-standoff-intense-damaging-7597664.php.
173.Visa issuances: U.S. Department of State, "Report of the Visa Office," 2017, https://travel.state.gov/content/travel/en/legal/visa-law0/visa-statistics/annual-reports.html; U.S. Department of State, "Classes of Nonimmigrants Issued Visas (Detailed Breakdown)," 1991, https://travel.state.gov/content/dam/visas/Statistics/Non-Immigrant-Sta…; U.S. Department of State, "Classes of Nonimmigrants Issued Visas (Detailed Breakdown)," 1996, https://travel.state.gov/content/dam/visas/Statistics/Non-Immigrant-Sta…; Asylees-Visa Waiver Program: U.S. Department of Homeland Security, "Yearbook of Immigration Statistics," November 14, 2017, https://www.dhs.gov/immigration-statistics/yearbook ; and Immigration and Naturalization Service, "Statistical Yearbook, 1978–1995," U.S. Citizenship and Immigration Services, August 9, 2017, https://www.uscis.gov/history-and-genealogy/historical-library/our-coll…. Refugees: U.S. Department of State, "Admissions & Arrivals," February 28, 2018, http://www.wrapsnet.org/admissions-and-arrivals/.
174. U.S. Census Bureau, Population Division, "Annual Estimates of the Resident Population for Incorporated Places of 50,000 or More, Ranked by July 1, 2016 Population: April 1, 2010 to July 1, 2016," May 2017, https://factfinder.census.gov/faces/tableservices/jsf/pages/productview.xhtml.
175. The majority of short-term admissions from Canada and Mexico are excluded, as noted in Department of Homeland Security, "Yearbook of Immigration Statistics 2015: Table 28," https://www.dhs.gov/immigration-statistics/yearbook/2015/table28. For the 185 million border entries annually from Mexico, see Miriam Valverde, "Trump Says 1 Million Legal Crossings along U.S.-Mexico Border," Politifact, September 14, 2016, http://www.politifact.com/truth-o-meter/statements/2016/sep/14/donald-t…. For the nearly 30 million border entries annually from Canada, see Canada Free Press, "Fewer Canadians Being Refused Entry at U.S. Land Border," CBC News, March 26, 2017, http://www.cbc.ca/news/canada/canada-us-border-fewer-refusal-customs-pr….
176. The terrorists were Gazi Ibrahim Abu Mezer (caught and released), Abdelghani Meskini (stowed away on a boat), Mahmoud Youssef Kourani (Mexican border), and Glen Francis (was a Trinidadian immigrant who immigrated to Canada before coming to live in the United States illegally). Abu Mezer: Benjamin Weiser, "U.S. Case against Informer Bares a Tangled Bond," New York Times, October 17, 2010, https://www.nytimes.com/2010/10/18/nyregion/18informer.html. Meskini: Office of the Inspector General, "Bombs in Brooklyn," Department of Justice, https://oig.justice.gov/special/9803/brbrp1.htm. Mahmoud: United States of America v. Mahmoud Youssef Kourani, "Indictment," United States District Court Eastern District of Michigan Southern Division, No. 03-81030, November 19, 2003, news.findlaw.com/cnn/docs/terrorism/uskourani111903ind.pdf. Francis: Kim Smith, "Trial Opens in 1990 Slaying of Teacher at Tucson Mosque," Arizona Daily Star, December 12, 2012, http://tucson.com/news/local/crime/trial-opens-in-slaying-of-teacher-at…. Illegal entries (extrapolated through 2016): Robert Warren and Donald Kerwin, "Beyond DAPA and DACA: Revisiting Legislative Reform in Light of Long-Term Trends in Unauthorized Immigration to the United States," Journal on Migration and Human Security 3, no. 1 (2015): 90, http://jmhs.cmsny.org/index.php/jmhs/article/view/45. Apprehensions: United States Border Patrol, "Nationwide Illegal Alien Apprehensions Fiscal Years 1925–2017," Customs and Border Protection, 2017, https://www.cbp.gov/sites/default/files/assets/documents/2017-Dec/BP%20….
177. Charles Doyle, "Terrorist Material Support: An Overview of 18 U.S.C. §2339A and §2339B," Congressional Research Service, December 8, 2016, https://fas.org/sgp/crs/natsec/R41333.pdf.
178. David Cole and James X. Dempsey, Terrorism and the Constitution (New York: New Press, 2006), p. 14.
179. Cole and Dempsey, Terrorism and the Constitution.
180. Glen Francis and Mahmoud Youssef Kourani.
181. Federal Bureau of Investigation, "Uniform Crime Reporting: Crime in the United States," https://ucr.fbi.gov/crime-in-the-u.s.
182. A. Trevor Thrall and Erik Goepner, "Step Back: Lessons for U.S. Foreign Policy from the Failed War on Terror," Cato Institute Policy Analysis no. 814, June 26, 2017, https://www.cato.org/publications/policy-analysis/step-back-lessons-us-foreign-policy-failed-war-terror.
183. Thrall and Goepner, "Step Back: Lessons for U.S. Foreign Policy from the Failed War on Terror."
184. U.S. Department of State, "Calculation of the Adjusted Visa Refusal Rate for Tourist and Business Travelers under the Guidelines of the Visa Waiver Program," https://travel.state.gov/content/dam/visas/Statistics/Non-Immigrant-Statistics/refusalratelanguage.pdf.
185. Comments of Leon Rodriguez, "Transcript of USCIS-DOS-HHS Press Call on Syrian Refugee Processing," U.S. Citizenship and Immigration Services, August 9, 2016, https://www.uscis.gov/news/news-releases/transcript-uscis-dos-hhs-press-call-syrian-refugee-processing.
186. U.S. Department of State, "U.S. Refugee Admissions Program FAQs," January 20, 2017, https://www.state.gov/j/prm/releases/factsheets/2017/266447.htm.
187. United Nations High Commissioner for Refugees, "Figures at a Glance," 2016, http://www.unhcr.org/en-us/figures-at-a-glance.html.
188. United Nations High Commissioner for Refugees, "UNHCR Resettlement Handbook: Country Chapter—The United States of America," http://www.unhcr.org/3c5e5a764.pdf.
189. Haeyoun Park and Larry Buchanan, "Refugees Entering the U.S. Already Face a Rigorous Vetting Process," New York Times, January 29, 2017, https://www.nytimes.com/interactive/2017/01/29/us/refugee-vetting-process.html.
190. Elliott, "The Shoe Bomber’s World."
191. Elliott, "The Shoe Bomber’s World."
192. U.S. Department of State, "Visa Waiver Program."
193. Lisa Seghetti and Stephen Viña, "U.S. Visitor and Immigrant Status Indicator Technology (US-VISIT) Program," Congressional Research Service, February 23, 2005, https://fas.org/sgp/crs/homesec/RL32234.pdf.
194. John Solomon, "Visa Denial Was Reversed for Terrorism Suspect in 2004," Washington Post, March 25, 2010, http://www.washingtonpost.com/wp-dyn/content/article/2010/03/24/AR2010032403092.html.
195. Solomon, "Visa Denial Was Reversed for Terrorism Suspect in 2004."
196. Jacobs, Testimony on "The Lessons and Implications of the Christmas Day Attack."
197. Eric Schmitt and Eric Lipton, "Officials Point to Suspect’s Claim of Qaeda Ties in Yemen," New York Times, December 26, 2009, http://www.nytimes.com/2009/12/27/us/27terror.html.
198. Susan Carroll, "Islamic School Confirms Terror Suspect Studied in Houston," Houston Chronicle, December 29, 2009, http://www.chron.com/news/houston-texas/article/Islamic-school-confirms-terror-suspect-studied-in-1727861.php.
199. John Mueller, ed., Terrorism Since 9/11: The American Cases (Columbus: Ohio State University, March 2016).
200. Jacobs, Testimony on "Hearing on The Lessons and Implications of the Christmas Day Attack."
201. Government Accountability Office, "Secure Flight: TSA Should Take Additional Steps to Determine Program Effectiveness," GAO-14-531, September 2014, http://www.gao.gov/assets/670/665676.pdf.
202. "Flight 253: Learning Lessons from an Averted Tragedy," Hearing before the House Committee on Homeland Security, January 27, 2010, https://www.gpo.gov/fdsys/pkg/CHRG-111hhrg56189/html/CHRG-111hhrg56189.htm.
203. Jacobs, Testimony on "The Hearing on the Lessons and Implications of the Christmas Day Attack."
204. Jacobs, Testimony on "The Hearing on the Lessons and Implications of the Christmas Day Attack."
205. Jacobs, Testimony on "The Hearing on the Lessons and Implications of the Christmas Day Attack."
206. Chuck Grassley, "Grassley Seeks Information about Failure to Revoke Visas to ‘Possible Terrorists’ and Presses State Department for Answers on Visa Screening Upgrades at Foreign Stations," January 11, 2010, https://www.grassley.senate.gov/news/news-releases/grassley-seeks-information-about-failure-revoke-visas-%E2%80%9Cpossible-terrorists%E2%80
%9D-and.
207. Matthew Wald, "Airport Efforts to Detect Explosives Expand," New York Times, February 17, 2010, http://www.nytimes.com/2010/02/18/us/18tsa.html.
208. Eric Schmitt, "New Teams Connect Dots of Terror Plots," New York Times, January 29, 2010, http://www.nytimes.com/2010/01/30/us/30intel.html.
209. U.S. Department of Homeland Security, "Implementing 9/11 Commission Recommendations."
210. BBC News, "Bomb Suspect Umar Farouk Abdulmutallab on UK Watch-list," BBC News, December 29, 2009, http://news.bbc.co.uk/2/hi/uk_news/8432180.stm.
211. James Gordon Meek, Ciny Galli, and Brian Ross, "Exclusive: US May Have Let ‘Dozens’ of Terrorists into Country as Refugees," ABC News, November 20, 2013, http://abcnews.go.com/Blotter/al-qaeda-kentucky-us-dozens-terrorists-country-refugees/story?id=20931131.
212. Meek, Galli, and Ross, "Exclusive."
213. Meek, Galli, and Ross, "Exclusive."
214. United States of America v. Abdinasir Mohamud Ibrahim, "Criminal Complaint," U.S. District Court for the Western District of Texas, Case No. 14-00108, February 3, 2014, https://www.investigativeproject.org/documents/case_docs/2619.pdf.
215. Government Accountability Office, "Refugees: Actions Needed by State Department and DHS to Further Strengthen Applicant Screening Process and Assess Fraud Risks," GAO-17-106, July 2017, http://www.gao.gov/assets/690/686310.pdf.
216. Government Accountability Office, "Actions Needed by State Department and DHS."
217. United States of America v. Jubair Ahmad, "Defendant’s Position with Regard to Sentencing Factors," Case No. 11-00054, February 7, 2012, https://object.cato.org/sites/cato.org/files/wp-content/uploads/ahmadjubairsentencingmemo.pdf.
218. Justin Fishel, Benjamin Siegel, and Emily Shapiro, "Inside the Immigration File of San Bernardino Shooter Tashfeen Malik," ABC News, December 2015, http://abcnews.go.com/US/inside-immigration-file-san-bernardino-shooter-tashfeen-malik/story?id=35912170.
219. Richard Serrano, "Tashfeen Malik Messaged Facebook Friends about Her Support for Jihad," Los Angeles Times, December 14, 2015, http://www.latimes.com/local/lanow/la-me-ln-malik-facebook-messages-jihad-20151214-story.html.
220. Al Baker and Marc Santora, "San Bernardino Attackers Discussed Jihad in Private Messages, F.B.I. Says," New York Times, December 16, 2015.
221. David Donahue, "The Security of U.S. Visa Programs," before the Senate Committee on Homeland Security and Governmental Affairs, March 15, 2016, https://object.cato.org/sites/cato.org/files/wp-content/uploads/testimony-donahue-2015-03-15_2.pdf.
222. Evan Perez and Dana Ford, "San Bernardino Shooter’s Social Media Posts on Jihad Were Obscured," CNN, December 14, 2015, http://www.cnn.com/2015/12/14/us/san-bernardino-shooting/index.html.
223. Mark Hamm and Ramón Fredrik Johan Spaaij, The Age of Lone Wolf Terrorism (New York: Columbia University Press, 2017), p. 221, https://object.cato.org/sites/cato.org/files/wp-content/uploads/nafisquaziageoflonewolfterrorismp221.jpg; and United States of America v. Mahmoud Amin Mohamed Elhassan, "United States’ Memorandum in Aid of Sentencing," Eastern District of Virginia, February 22, 2017, https://www.investigativeproject.org/documents/case_docs/3247.pdf.
224. United States of America v. Khalid Ali-M Aldawsari, "Criminal Complaint," Northern District of Texas, Case No. 11-017, February 23, 2011, https://www.investigativeproject.org/documents/case_docs/1488.pdf.
225. John Sowell, "Kurbanov Sent to Prison for 25 Years in Boise Terror Plot," Idaho Statesmen, January 7, 2016, http://www.idahostatesman.com/news/local/crime/article53610300.html; and Ellen Knickmeyer, "Details Emerge in Alleged Army Rape, Killings," Washington Post, July 3, 2006, A15, http://www.washingtonpost.com/wp-dyn/content/article/2006/07/02/AR20060….
226. "Smadi has repeatedly indicated to both FBI UCE2 and FBI UCE2 that he came to the United States with the purpose of committing ‘Jihad for the sake of God.’": United States of America v. Hosam Maher Husein Smadi, "Warrant for Arrest," U.S. District Court for Nothern District of Texas, September 24, 2009, https://www.investigativeproject.org/documents/case_docs/1074.pdf. Reasons to question this include that his father made the decision to send him to live in California. In 2008, before his encounters with law enforcement, he told friends that he moved to the United States because Jordan was "really strict," and he "wanted freedom." During this time, he smoked marijuana and drank alcohol. His friends and family noticed a personality change about a year before his arrest. See James McKinley Jr., "Friends’ Portrait of Texas Bomb Plot Suspect at Odds with F.B.I.,"New York Times, September 27, 2009, http://www.nytimes.com/2009/09/28/us/28texas.html?pagewanted=all&_r=0 ; and Jason Trahan, "Dallas Bombing Plotter Hosam Smadi Sentenced to 24 Years in Prison," Dallas Morning News, October 20, 2010, https://www.dallasnews.com/news/news/2010/10/20/20101019-Dallas-bombing….
227. IPT News, "Indicted USF Student Has Terror Past in Egypt," Investigative Project on Terrorism, September 5, 2007, https://www.investigativeproject.org/426/indicted-usf-student-has-terror-past-in.
228. United States of America v. Ahmed Abdellatif Sherif Mohamed, "Sentencing Memorandum," U.S. District Court Middle District of Florida Tampa Division, Case No. 07-00342, November 4, 2008, https://www.wired.com/images_blogs/threatlevel/files/remote.
pdf.
229. United States of America v. Ahmed Abdellatif Sherif Mohamed, "Sentencing Memorandum."
230. Benjamin Powell, "Coyote Ugly: The Deadweight Cost of Rent Seeking for Immigration Policy," Public Choice 150 (2012): 195–208, https://link.springer.com/article/10.1007/s11127-010-9698-2; World Travel and Tourism Council, "Travel & Tourism: Economic Impact 2015, United States of America," p. 5, https://zh.wttc.org/-/media/files/reports/economic-impact-research/regi…; and George Borjas, "Immigration and the American Worker: A Review of the Academic Literature," Center for Immigration Studies, April 2013, p. 2, https://cis.org/Report/Immigration-and-American-Worker.
231. National Academies of Sciences, Engineering, and Medicine, The Economic and Fiscal Consequences of Immigration (Washington: National Academies Press, 2017), https://doi.org/10.17226/23550.
232. Nowrasteh, "Terrorism and Immigration: A Risk Analysis."
233. Jiawei Li, Simon Pollard, Graham Kendal, Emma Soane, and Gareth Davies, "Optimising Risk Reduction: An Expected Utility Approach for Marginal Risk Reduction during Regulatory Decision Making," Reliability Engineering and System Safety, May 2009, .http://www.cs.nott.ac.uk/~pszjl/index_files/RESS.pdf.
234, "Uniform Crime Reporting."

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.